WikiLeaks publishes MacBook, iPhone hacking toolkit supposedly used by CIA

WikiLeaks published Thursday a new batch of supposed CIA documents that reveal how the spy agency has hacked into Apple computers and smartphones over the last decade. The 12 newly released folders provide insight into some of the CIA’s methods and techniques, which evidently require physical access to compromise a target device in many cases.
Cybersecurity researchers tell CyberScoop that the documents, some of which are marked as recent as 2013, generally prove that the CIA boasts a “robust” Mac attack toolkit. The spy agency was “ahead of the curve versus public disclosure” for many of these capabilities, said Apple security researcher Pedro Vilaça.
A WikiLeaks press releases reads, “these documents explain the techniques used by CIA to gain ‘persistence’ on Apple Mac devices, including Macs and iPhones and demonstrate their use of EFI/UEFI and firmware malware.”
UEFI stands for Unified EFI Specification, which defines an interface between the operating system and platform firmware. It’s predecessor is known as the EFI Specification. UEFI, and EFI before it, support an operating system’s boot process.
Tools
One of the capabilities mentioned in the leaked documents, codenamed “Sonic Screwdriver” and dated 2012, requires an operator to infect a Mac with malware stored inside a Thunderbolt-to-Ethernet adapter. Once installed onto an asset’s device, it is impossible for the computer to be restored to factory default settings. Sonic Screwdriver is not a malware variant, but rather it can be understand as a construct that allows for an attacker to bypasses an enabled firmware password to deliver malicious code.
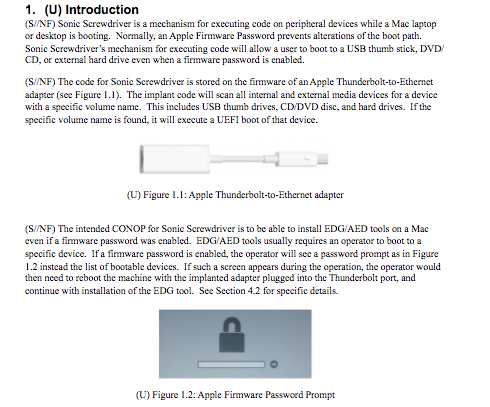
Supposed CIA documents published by WikiLeaks — “Dark Matter” series
The Sonic Screwdriver capability shares some similarities with a technique developed by researcher Trammel Hudson, which he showcased in 2014, and another method presented in 2012 at the Black Hat cybersecurity conference by a researcher known as Snare.
Another, different document, dated November 2008, describes a malware variant, dubbed “DarkSeaSkies,” that again requires an operator to have physical access to a MacBook. In theory, DarkSeaSkies would be installed onto a target device using something like Sonic Screwdriver.
DarkSeaSkies runs in the background of a MacBook Air, providing the attacker with command and control capabilities, including file transferring. The implant requires that the laptop be internet connected. If the virus cannot communicate with a “listening post” then it will automatically self-destruct after some period of time. This uninstallation features appears to be designed to thwart digital forensic efforts.
The use of USB-to-Ethernet dongles to install malware seems to suggest that that some of these exploits were likely used on single targets and not for some massive surveillance campaign, explained Jonathan Nichols, a senior analyst with cybersecurity firm ZeroFOX.
Controversy
An early point of controversy in the latest document dump has come from the fact that WikiLeaks claims one of the listed exploits, named “NightSkies,” was “designed to be physically installed onto factory fresh iPhones. i.e the CIA has been infecting the iPhone supply chain of its targets since at least 2008.”
The documents published by the transparency organization, however, do not provide information revealing any CIA operation involving the infiltration of Apple factories or interception of large batches of iPhones to install malware.
Like DarkSeaSkies, NightSkies requires physical access to install onto a smartphone. The malware is intended for an iPhone that’s never been turned on before — hence the “factory fresh” description by WikiLeaks.

Supposed CIA documents published by WikiLeaks — “Dark Matter” series
Based on how it is described in one document dated July 2008, NightSkies is a “beacon/loader/implant tool for the Apple iPhone 3G v2.1 … [the malware] operates in the background providing upload, download and execution capability on the device.”
“When the implanted iPhone is first turned on, it will need to be activated before it can be used. Insert a SIM card and connect the iPhone via USB to iTunes,” a user manual for NightSkies published by WikiLeaks explains, “the iPhone will phone home to Apple over the Internet before it will be activated, so sufficient steps should be taken to protect networks and hardware.”
Cybersecurity research Nicholas Weaver said that WikiLeaks’ supply chain claim is misleading.
“If somebody has physical access to your computer, you can’t call it yours anymore,” Weaver told CyberScoop, “installing onto ‘factory fresh’ is not about interdiction but targeted delivery: the CIA asset gives the target a phone or a MacBook, this is the general extent of the ‘supply chain’ the CIA is concerned with.”
He added, “Interdiction in the ‘supply chain’ works very well for things like routers, which are big, expensive, few in number, shipped from the US, and to known customers … [but] It doesn’t work for something you can buy at a local store or which is drop-shipped from a local warehouse in the country where it’s going to be used.”
Classified NSA documents previously obtained by journalist Glenn Greenwald showed that agency employees in 2010 would intercept internet routers and install beacon implants onto the devices before they arrived at a target address. Though WikiLeak’s CIA documents do not show the CIA performing a similar type of operation, the possibility exists.
Thursday’s CIA document dump, dubbed “Dark Matter,” comes three weeks after WikiLeaks posted a larger trove of classified CIA documents to their website, detailing a wide array of different digital espionage capabilities that are aimed at specific software products developed by popular technology companies. Shortly thereafter, WikiLeaks Editor-in-Chief Julian Assange said in a press conference live streamed to Twitter that, “less than 1 percent” of the CIA material acquired by the transparency organization had been published.
WikiLeaks claims that a disgruntled defense contractor handed the CIA files to WikiLeaks.