Talos: Android trojan resembling Play Store installs sophisticated spyware

A newly uncovered Android trojan can install advanced spyware on unsuspecting users’ phones under the guise that it’s just part of the operating system, according to research from Cisco Talos out Thursday.
Talos says that the malware’s sophistication is “of an uncommonly high level, making it a dangerous threat.” Vitor Ventura, who authored the Talos report, told CyberScoop by email that it “appears to be a new family of malware.”
After being installed and going through some onboarding procedures, the “GPlayed” trojan has a broad range of spying capabilities. It can exfiltrate information like texts and contacts, track geolocation, change the lockscreen password and collect payment credentials.
Beyond that, the trojan has the built-in ability to adapt after being installed, Talos says. It load new plugins remotely, inject new scripts and compile new code.
“This means that the authors or the operators can add capabilities without the need to recompile and upgrade the trojan package on the device,” the report says. “This is a full-fledged trojan with capabilities ranging from those of a banking trojan to a full spying trojan.”
GPlayed is another reason to be cautious around the practice of downloading Android apps from outside the Google Play Store, Talos says. The trojan appears to do a pretty decent job of disguising itself as something innocuous.
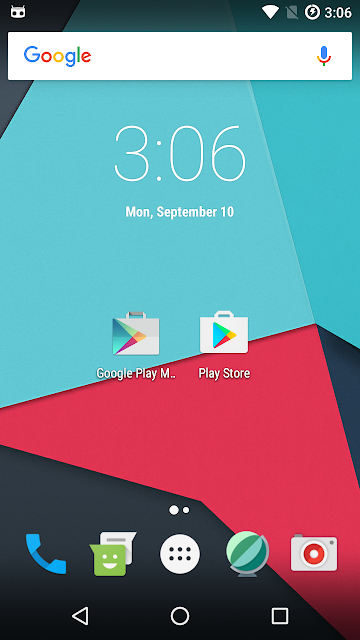
The sample observed by Talos looks like the Google Play Store on a user’s home screen, with a similar icon and the name “Google Play Marketplace.” After being installed, the trojan asks the user for administrator privileges and for payment data in order to use Google services, all in dialogues that closely resembles what happens when Android legitimately asks to collect that information. Ventura said the malware likely targets “regions where there is no official app store or people who are looking for apps distributed outside of the app store.”
User dialogues in the analyzed samples are in Russian, but Talos says it would be “extremely easy” to adapt it into a different language because its highly customizable.
(Cisco Talos)
The researchers say the GPlayed trojan is probably in a testing phase. Ventura said Talos has been observing GPlayed for a few months and “it seems to be limited in use” so far. The word “test” is in a lot of labels and strings, and the researchers say they’ve observed the malware being tested on antivirus testing platforms, likely to see how well it’s detected.
Talos says that GPlayed shows that third-party Android apps continue to be a security risks of unknowing users.
“There have been several recent examples of companies choosing to release their software directly to consumers, bypassing traditional storefronts. The average user might not have the necessary skills to distinguish legitimate sites from malicious ones.”
One example of this is a slew of fake “Fortnite” apps making themselves out to be the popular online game, but actually install spyware on victims’ phones. The apps preyed on Android users eager to play the game, which had for long only been available on major gaming platforms and iOS.
Incidentally, “Fortnite” for Android is also out for all Android users Thursday — downloadable only from the developer.




