Shadow Brokers latest leak a gold mine for both criminals and researchers

As information security enthusiasts continue to pour over the Shadow Brokers latest dump, the alleged cache of NSA tools is turning out to be a treasure trove for both researchers and criminals.
Ransomware known as “AES-NI” has been updated with a so-called “NSA Exploit Edition” that the malware’s developer claims is now using EsteemAudit and EternalBlue exploits to infect machines, encrypt files and demand ransom for release. EsteemAudit and EternalBlue were two tools dumped in last week’s leak.
A rash of forum posts show several ransomware victims running old, unpatched or unsupported Windows servers that have been infected. There has been no independent confirmation on how the new ransomware works, but the malware’s author claimed to CyberScoop that they are using NSA exploits.
“We use SMB [Server Message Block] and RDP [Remote Desktop Protocol] exploits: Esteemaudit, Eternalblue,” the developer said. “They all are in public now.”
Liam O’Murchu, the director of Symantec’s security technology and response group, said EsteemAudit and EternalBlue “are some of the easier tools to pick up and to a certain degree they could be the most dangerous depending on how they’re used.”
O’Murchu had not yet examined AES-NI malware, but said both of the Shadow Brokers-supplied tools cited by the developer are relatively easy to pick up because the source code is available in the April 8 leak and older unsupported machines remain unpatched and vulnerable to the attacks.
“I have just written the specific payload DLL and injected it to the process on the remote machine using that exploits,” the malware’s author wrote in an email. “I want to mention that NSA specialists did excellent work creating very powerful and highly customizable hacking tools. They even have their own framework like Metasploit.”
Metasploit is penetration testing software that allows an attacker to easily and efficiently exploit a target using a readily-available arsenal of tools. The NSA version of the framework, which was released last Friday, is known as Fuzzbunch.
“If one thing fails, they just move on to the next tool,” O’Murchu said. “And the next and next until they find something that works. It was interesting to see you need [to] have everything right, patched and locked down because the attackers have this suite of tools to scan your environment and find one thing configured incorrectly to abuse. It gives us insight into the ease the attackers have when they launch attacks.”
Whether or not AES-NI is in fact using NSA exploits, experts expect criminals to adapt the tools for their own use.
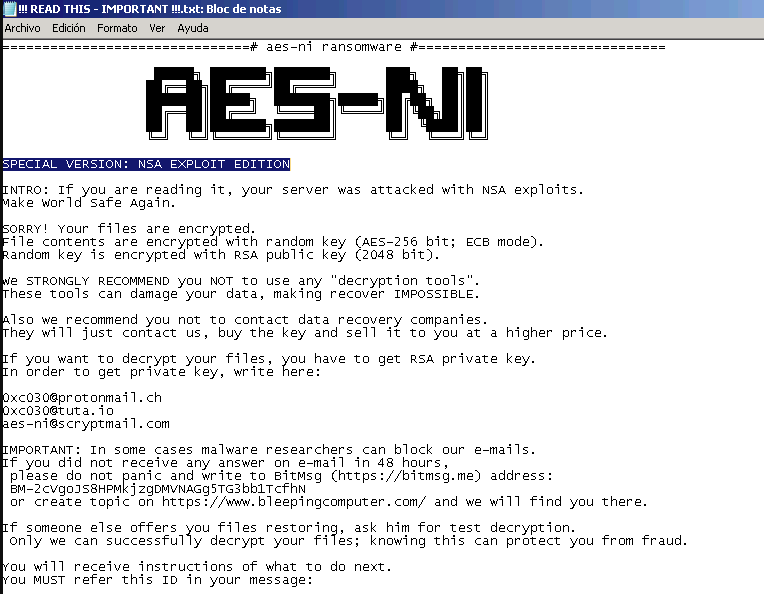
The ransom note seen this weekend by AES-NI’s victims.
O’Murchu’s team at Symantec worked through the weekend analyzing the mountain of data released Friday by the mysterious group. Despite no zero-days being included in the leak, O’Murchu’s team has found operational notes and tools in the leak that shed light on exactly how these attackers work.
“We’ve seen operational notes about attacks that were being carried out and how they’re carried out,” O’Murchu said. “There notes about what they did, what exploits are used, how successful they were, how long they were on the box, what information they gathered, the layout of the network.”
O’Murchu’s team has long followed and profiled NSA attackers, including examinations of the tools originally described in the Edward Snowden leaks from 2013. The main boon is the “strategic” knowledge for what security policies and procedures may be needed to bolster defense.
“And then there’s information about what tools they’re using,” O’Murchu explained. “We see information about tools for building malware, for example, tools for running the server side and communicating with the malware. And in once case there’s a manual in there for setting up the endpoint malware and the server side script for communicating with the malware. We see a lot of tools that would allow the attackers to get into machines, explore the network or move laterally to steal a password and a variety of things.”
Former intelligence officers also told CyberScoop that the same information can be gleaned from Linux tools that were leaked by the Shadow Brokers earlier this month.
While EsteemAudit and EternalBlue are relatively easy to quickly weaponize, there are likely more attacks on the horizon in the form leaked implants incorporated into new malware campaigns.
The AES-NI malware developer, for his part, said he was already making money with his new ransomware campaign. Judging by the cries for help popping up on tech support forums around the web, it’s clear at least that attacks are under way. The details, including the exploits used and money made, remain unconfirmed so far.




