Fileless DNS malware used in SEC-filing cyberattacks
DNSMessenger, the new super-stealthy malware that uses the internet’s address system as a command and control channel is being employed in a financial fraud spear-phishing campaign — targeting executives in large public companies involved with filings to the Securities and Exchange Commission.
Threat researchers at FireEye reported the SEC campaign this week, clearing up the mystery which had surrounded DNSMessenger since it was identified at the weekend by Cisco Talos: Who was it aimed at?
“We view this [attack] as one component of a very sophisticated, financially motivated cybercrime campaign” by an actor FireEye has dubbed Fin7, the company’s Threat Intelligence Manager John Miller told CyberScoop in an interview.
Spear phishing uses carefully crafted fake emails carrying malicious attachments or links — click and the malware is activated. In the case of the new Fin7 campaign, the emails appeared to come from the SEC’s online filing system EDGAR, and the attachment was a word document titled “Important changes to form 10K.”
A 10K is a form that public companies have to submit to the SEC every year, and the targets were people involved in their company’s filings — often meaning their email address was listed on public documents.
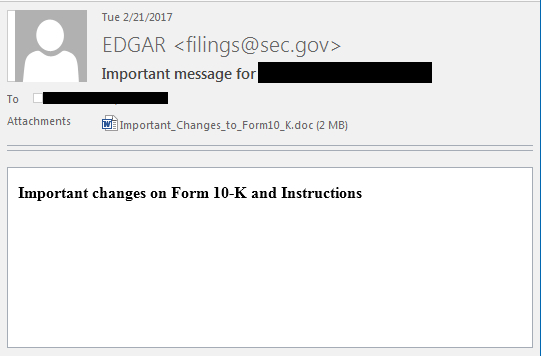
A spear phishing email from the Fin7 SEC campaign (Source:FireEye)
Miller said because FireEye’s security systems had thwarted the would-be attackers, there was no way of knowing for sure what they would have done, had they been able to seize control of the computers and accounts of the targeted executives.
But given the track record and the targets, he said it was “very possible that they were interested in securities fraud in some manner.”
FireEye said in its blog posting that the malware had been found attacking 11 companies in several sectors, but mostly financial.
Fin7 emerged several years ago as a threat group using advanced malware to steal credit card data from point-of-sale systems, Miller said. Since then, it has also been associated with the Carbanak malware, which targeted bank ATM systems.
He said they were a “medium-high” sophisticated threat actor, “Maybe around a seven,” on a 1-10 scale.
DNSMessenger is a highly stealthy malware. Rather than installing itself on the targeted computer’s hard drive, it pulls down commands using the domain name system, or DNS, the internet’s address protocol. This makes it very hard to detect, since most enterprises don’t filter or monitor their DNS traffic.
But, like all spear phishing, it initially relies on the user to click: In this case, the victim is asked to “enable content,” on the document when it is downloaded. That allows a Visual Basic script to run which begins the take-over process.
Miller said FireEye had seen no evidence of the multi-stage malware, which FireEye dubs “PowerSource” and “TextMate,” being used outside of the SEC campaign.
But Craig Williams, senior technical leader and global outreach manager of Cisco Talos, told CyberScoop his researchers had found samples with “different background images and different sender,” suggesting the malware was being sued ion other campaigns as well.
Williams said the data Cisco had was anonymized so it lacked contextual information about the targets, but they had seen enough variation in the lures and delivery strategy to make them believe DNSMessenger was “kit-based.”
“They’ve got a little production line going there,” he said, adding “It’s clearly very targeted, we don’t see much of it.”
Miller said that though the malware was fileless in the sense it did not install itself on the hard drive, it did leave “some traces or artifacts in the file system registry.”




