Pentagon lays out plan to secure websites in response to lawmaker inquiry
The Department of Defense says it has a plan to make sure that all of its public-facing websites are configured in a way that doesn’t put the security of their visitors at risk.
In a letter responding to a lawmaker dated July 20, DOD Chief Information Officer Dana Deasy wrote that the department plans by the end of 2018 to fix issues with trust certificates and encryption that are present across many websites affiliated with it. Certain issues will take longer, he said, will at least have a definitive plan by the end of the year.
“The Department is working hard to ensure DoD inspires trust among citizens and partners in its digital interactions across our missions, business, and entitlements roles,” Deasy wrote.
Deasy laid out the plan in response to a May letter from Sen. Ron Wyden, D-Ore., that raised questions about the issue of insecure websites. Wyden initially reached asking the department to implement proper encryption and protection on all of its public-facing websites. At present, many of the DOD’s websites don’t use adequate certificates or up-to-date encryption, which in many cases leads users to a browser message warning them that attackers could be trying to steal their information.
“These warnings will erode the public’s trust in the Department and its ability to defend against sophisticated cyber threats,” Wyden wrote at the time.
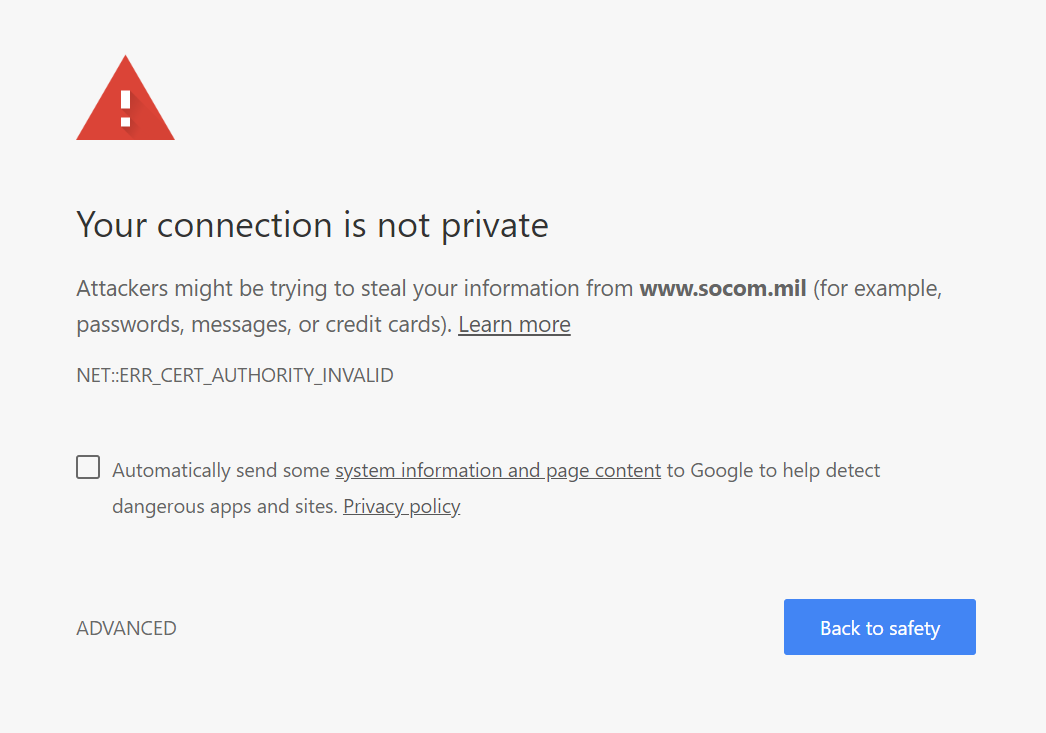
A message displayed by the Google Chrome browser when trying to visit the website for U.S. Special Operations Command.
One of the issues Wyden initially pointed out is that many DOD websites don’t employ HTTPS, the web protocol intended to ensure secure connections and protect against man-in-the-middle attacks. Deasy’s response letter says that DOD is directing all its public-facing websites to use HTTPS, rather than the outdated HTTP.
Deasy wrote that DOD will also phase out old certificates issued by the department that Wyden said many browsers deem untrustworthy, and instead use commercially available certificates. In the meantime, the department will work in improving its own certificate process.
“DoD will issue direction to implement commercial publicly trusted certificates on DoD’s public-facing sites and services while we complete work on the Federal/DoD public trust [Public Key Infrastructure],” Deasy wrote.
The one holdup is the implementation of HSTS, a policy whereby a website forces a browser to use the secure HTTPS protocol. Deasy explains that a user could end up being denied service if a domain is improperly prepared for HSTS. The Department needs to conduct “thorough testing” to make sure that certain capabilities are “not hampered by the implementation of HSTS Preload,” he said.
So while other issues are to be mitigated by December 31, Deasy said, that’s when DOD will issue its plan to roll out HSTS.
Resolving these issues will ensure that the Pentagon is meeting requirements set by the Department of Homeland Security in October 2017.
“The Pentagon deserves credit for moving toward these commonsense cybersecurity improvements for their websites and email,” Wyden said in a statement provided to CyberScoop. “The men and women of the American military, and anyone who visits a Defense Department website, will be better-protected from spammers, scam artists and spies once these changes go into effect.”




