Pakistani military leverages Facebook Messenger for wide-ranging spyware campaign

Security researchers discovered two pieces of malware used by the Pakistani military in order to spy on specific targets in the Middle East, Afghanistan and India, according to the mobile security company Lookout.
The malware, dubbed Stealth Mango and Tangelo, appears to have successfully compromised government officials, medical professionals and civilians in Afghanistan, India, Iraq, Iran, the United Arab Emirates and Pakistan. Targets were compromised via Android and possibly iOS.
Government officials in the United States, Australia, the United Kingdom and Iran were indirectly compromised after interacting with direct Stealth Mango victims.
Instead of sophisticated and expensive exploits, attackers relied on phishing through third-party app stores and possibly physical access to targeted devices. The campaign was ongoing as of April 2018.
The malware, developed by independent contractors, is constantly being updated. Developers are releasing up to two new versions per week.
“What’s interesting is the ability, insight and amount of data they’re able to gather by having something as simple as they did with Stealth Mango,” said Andrew Blaich, a security researcher at Lookout. “No exploits, just an overly-permissive app they phish users into installing on to their phones in very targeted scenarios. They’re able to exfiltrate just about everything they need from a device without having to resort to exploits.”
The phishing primarily took place over Facebook Messenger. A user named “Sana” came up repeatedly in the data Lookout researchers saw. Blaich believes “Sana” to be a fake persona used to strike up a conversation with a target and then push them to a website where they can download the APK that will infect their phone. The infected APK is disguised to be a video calling application, but is used to spy on the target.
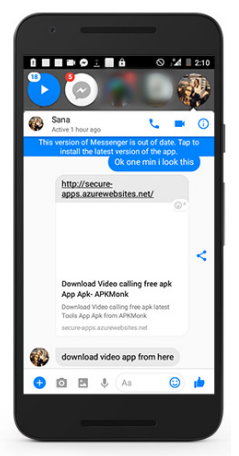
Screenshot: Lookout
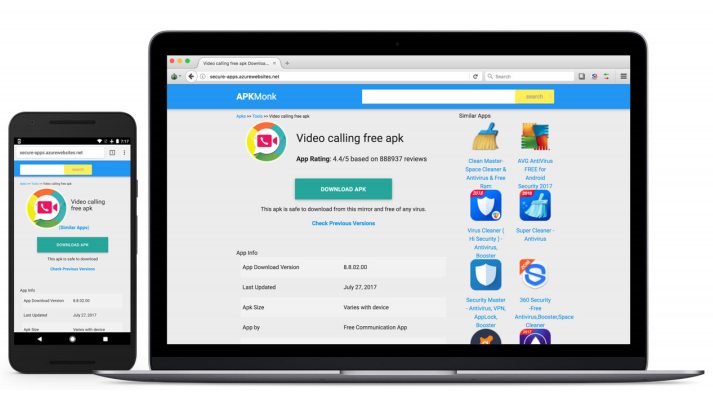
Screenshots: Lookout
“Google identified the apps associated with this actor, none of the apps were on the Google Play Store,” a Google spokesperson said. “Google Play Protect has been updated to protect user devices from these apps and is in the process of removing them from all affected devices.”
Lookout researchers discovered over 30GB of successfully stolen data including internal government communications, pictures of government documents including IDs and passports, GPS coordinates of pictures and devices, detailed travel information and reports as well as photos of weapons systems. The 30GB of data was gathered because the hackers accidentally left it publicly accessible on the internet.
Researchers said that officials from the U.S., Australia, Great Britain, NATO and Iran had their data inadvertently collected after interacting with a Stealth Mango or Tangelo victim.
From the U.S., the exfiltrated data includes sensitive letters from U.S. Central Command, as well as a letter from letter from the High Commission for Pakistan to the United States Director of the Foreign Security Office Ministry of Foreign Affairs. The data includes photos of U.S. military hardware and photos of military personnel. One example is shown here:

Exfiltrated data contained military photos with U.S. Army personnel. Credit: Lookout
The possibility of physical access is based on some of the exfiltrated data which includes a packaging slip that shows an infected phone was sent to a repair shop with links to an individual Lookout believes is linked to the malware’s developers.
The group responsible for this spying campaign is believed to be responsible for Operation C Major and Transparent Tribe, two 2016 hacking campaigns that chiefly targeted the Indian government.
Who built this?
Lookout said Stealth Mango and Tangelo were developed by a group of freelancers who have a long resume of surveillanceware start-ups and businesses, along with other apps they’ve developed. They pointed to a Freenlancer.com profile charging $50 per hour.
Code analysis of Stealth Mango “found multiple similarities to other commodity spyware families that fall into the category of ‘spouseware,’ or apps marketed as software that allow individuals to track and monitor the mobile devices of significant others or their children. Research into the program’s infrastructure has consistently linked back to several key individuals that we have identified as belonging to the same freelance developer group associated with Stealth Mango and Tangelo,” according to Lookout.
“We believe this freelance developer group built it and it looks like at least one member does work for the Pakistani military,” Blaich said. “Because of that connection as well as logins we see on the admin console sheds light on who is actually operating it: the Pakistani military.”
The main developer used the same email address to register domains for spyware families that are similar in code and heuristics to Stealth Mango, including spyware from a company called Ox-i-Gen Inc. TheOneSpy is billed as “the World’s most advance phone spy app” for parents that vacuums up all the data on an Android phone and hands it to parents.
Researchers successfully retrieved the compromised data due to several security mistakes by the hackers including “the presence of the web shell software WSO 2.5 hackers commonly use to maintain remote access to a server,” Lookout’s researchers explained. “It’s unclear whether WSO was installed by a third-party actor that successfully compromised this site or if the operators behind Stealth Mango installed and configured it themselves.”
The Pakistani Armed Forces did not respond to a request for comment.
Although Android phones look like the primary target for these campaigns, it is notable that iPhones — widely considered more secure and difficult to exploit than Android phones — are not completely exempt. However, the iOS malware that Lookout found, a sample Debian package on attacker infrastructure called Tangelo, requires the iPhone already be jailbroken in order to work. This differs from more sophisticated and expensive malware like Pegasus that accomplished a jailbreak on its own.
By contrast, a zero-day exploit that accomplished a remote jailbreak of an iPhone is currently going for $1.5 million at the public exploit-buying program Zerodium.
Zero-day exploits may get a lot of the headlines and hype, but cheap spyware and effective phishing are often all a hacker needs to get the job done.


