Dual North Korean hacking efforts found attacking Google Chrome vulnerability
Two distinct sets of North Korean hackers were exploiting the same remote code execution vulnerability in the Chrome web browser — one targeting news media and IT companies, the other aimed at cryptocurrency and fintech organizations — Google’s Threat Analysis Group announced Thursday.
The vulnerabilty, which was patched on Feb. 14, would have allowed the hackers to deliver malware packages in hidden iframes, both on websites they owned as well as websites they’d compromised. The two groups had different aims and used different techniques, but they used the same exploit kit, meaning they likely worked for the same entity with a shared supply chain, according to Adam Weidemann of the Threat Analysis Group, which published the findings to the group’s blog.
In one of the campaigns Google researchers saw the hackers make multiple attempts to use the exploit after the Feb. 14 patch, “which stresses the importance of applying security updates as they become available,” Weidemann wrote.
The campaign targeting unnamed news media and IT companies went after more than 250 people working for more than 10 different news media, domain registrars, web hosting providers and software vendors, Weidemann wrote. The targets were sent emails purporting to be from recruiters at Disney, Google and Oracle with phony job opportunities, with links that led to spoofed web pages for legitimate job search sites such as Indeed and ZipRecruiter.
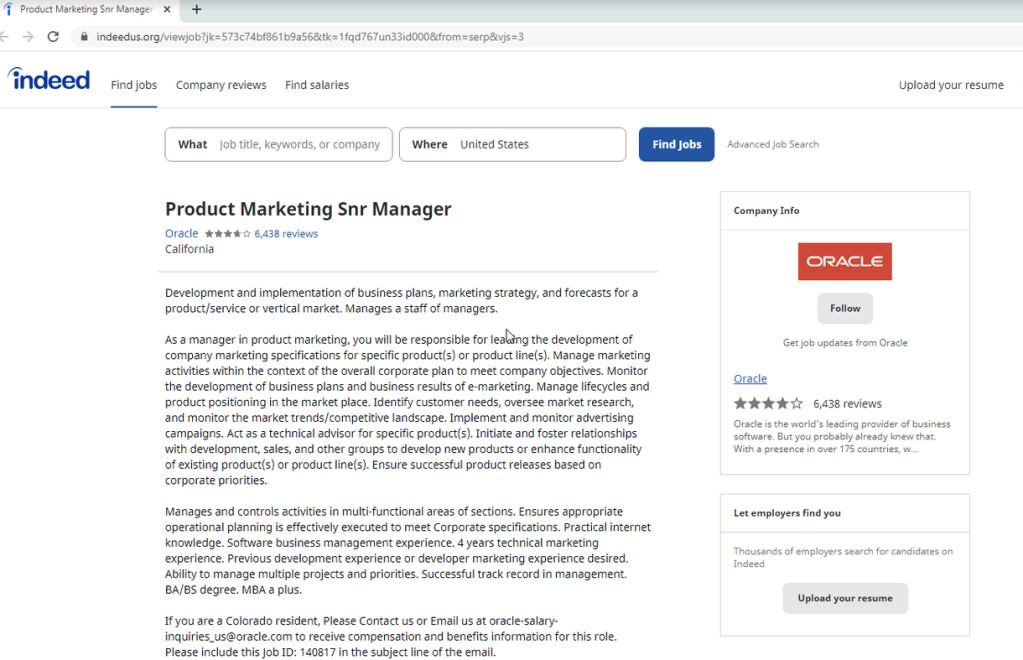
The fake job domains were close to the originals they were hoping to mimic, such asdisneycareers[.]net, find-dreamjob[.]com and indeedus[.]org. If the target clicked any of the links, they would trigger a hidden iframe that would deliver the exploit kit, Weidemann wrote.
The campaign with the phony job listings has direct infrastructure overlap with a campaign Google exposed in January 2021, where North Korean hackers established fake personas to target cybersecurity and information security researchers and journalists in a coordinated social engineering effort. Cybersecurity firm ClearSky previously analyzed and dubbed the campaign “Dream Job” in August 2020.
The other campaign exposed Thursday targeted more than 85 people in the cryptocurrency and fintech industries with the same exploit kit, Weidemann wrote. The campaign involved compromising at least two legitimate fintech company websites as well as fake websites set up to deliver malware through hidden iframes.
In both campaigns the hackers took strides to make it harder for security researchers to analyze their efforts, such as only serving the iframes at specific times, or encryption at multiple points along the exploitation chain.
The Google research comes a day after cybersecurity firm Mandiant, recently acquired by Google, released a detailed breakdown of the multiple North Korean hacking efforts taking place simultaneously, and which parts of the government are involved. North Korea’s government “possesses the flexibility and resilience to create cyber units based on the needs of the country,” which include espionage, destructive operations and financial crimes, the Mandiant researchers wrote. The hacking teams are used in cryptocurrency heists, targeting of media, news and political entities, international and nuclear information and the theft of COVID-19 vaccine research, the researchers concluded.




