Microsoft strikes back at Necurs botnet by preemptively disabling hacking tools

Microsoft is trying to sink a vast network that cybercriminals have used for eight years to spread spam and hack computers throughout the globe.
Microsoft announced on Tuesday that it has moved to disrupt the Necurs botnet, a network of more than 9 million computers that had been surreptitiously infected with malware and then used by hackers to carry out various schemes. Attackers, likely in Russia, according to Microsoft, used Necurs to distribute pharmaceutical spam, facilitate ransomware attacks and infect victims with numerous types of malicious software, such as the GameOver Zeus malware that is blamed for $100 million in losses.
“The Necurs is one of the largest networks in the spam email threat ecosystem, with victims in nearly every country in the world,” Tom Burt, Microsoft’s corporate vice president for customer security and trust, said in a statement. “During a 58-day period in our investigation, for example, we observed that one Necurs-infected computer sent a total of 3.8 million spam emails to over 40.6 million potential victims.”
A judge in the Eastern District of New York on March 5 authorized Microsoft to seize control of the American computers under Necurs’ control. From there, Microsoft says it systematically generated 6 million new domains likely to be taken over by the scammers behind Necurs within the next two years. Microsoft then reported those domains to the countries they were likely to affect, resulting in authorities blocking those pages to prevent them from being used in any attacks. Other companies in 35 countries helped with the effort, Microsoft said.
The company also is working with the web monitoring service BitSight, along with internet service providers, the computer emergency readiness teams and police in Mexico, Colombia, Taiwan, India, Japan, France Spain, Poland and Romania to enforce the takedown.
In its announcement, BitSight demonstrated how the Necurs operators built an international infrastructure by hacking computers in Africa, India and through the western hemisphere. India had the most infections, making up 13.59% of the botnet.
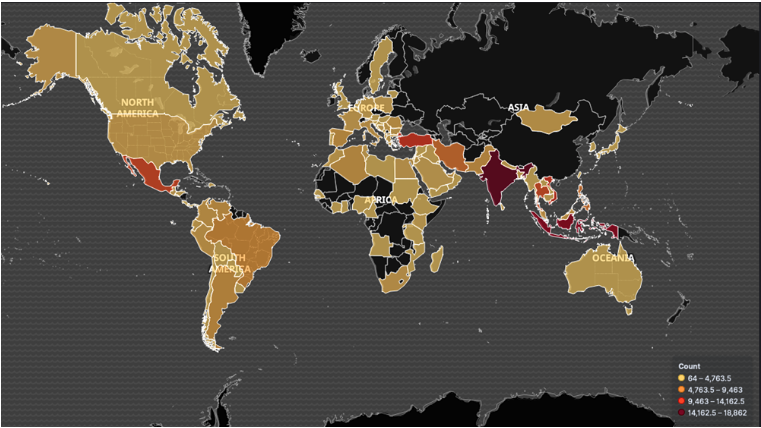
Necurs botnet infrastructure (via BitSight Technologies).
This operation is the result of an eight-year effort to track Necurs’ development. The takedown comes after Microsoft previously used court orders to shutter websites associated with suspected Iranian hackers. In 2018, Microsoft acted on another court order which authorized the technology giant to take down six websites used by a Russian government-linked hacking group.
Necurs was widely recognized for its ability to sneak malicious emails through spam filters. The hacking tool is survived by other botnets, such as Emotet, which continue to spew spam and aid hackers trying to reach a broader swath of victims.
The court documents from the Necurs case are available in full here.




