Monero mining botnet earns suspected Chinese hacker $25,000 per month

Mining cryptocurrencies can be a costly investment, but creative cybercriminals have found a money-making solution.
Researchers say a newly discovered botnet consisting of 15,000 machines is stealing computing power to mine increasingly valuable cryptocurrencies like Monero to enrich a hacker named “Bond007.01.”
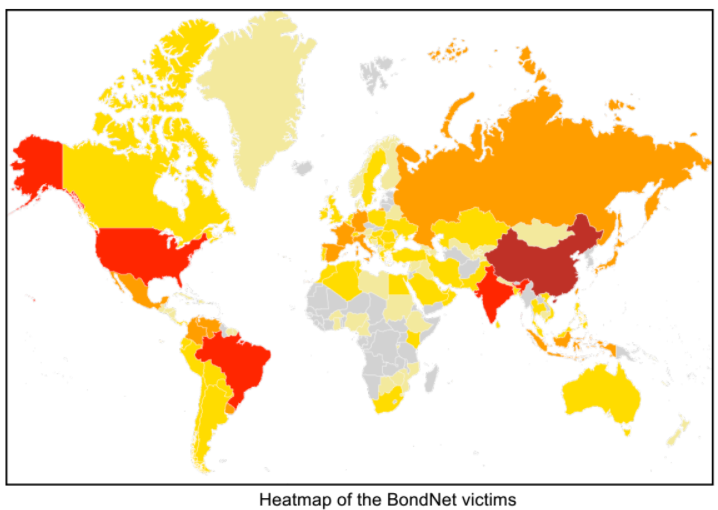
The entire “BondNet botnet” operation is netting around $25,000 per month, according to researchers at the Israeli security firm GuardiCore Labs. The victims include high-profile global companies, universities, city councils and other public institutions. They’re not losing money, just resources: Hackers have long known that when you don’t have to pay for the electricity powering the processors, cryptocurrency mining is pure profit. As bitcoin and its variants continue to rise to unprecedented value, the reward for such a scheme will increasingly outweigh the risk.
The price of Monero, a privacy-focused cryptocurrency that hides transactions, has risen 2,109 percent in the last year. The last month alone has seen a 44 percent rise in price.
Bond007.01 is suspected to be located in China, due to the use of copy-and-pasted code originating from Chinese websites, unique handling of Chinese desktop victims and the compiling of the BondNet C&C server on a Chinese computer, Ofri Ziv, GuardiCore’s vice president of research, told CyberScoop.
Bond007.01, who also goes by the alias leebond986, has a habit of reusing code via very simple constructs that lead researchers to believe it’s a single actor.
Bond007.01 uses a variety of old vulnerabilities and bad passwords to attack mostly old and unsupported Windows Servers machines. The most common attack vector uses MySQL to install a remote access Trojan (RAT) and cryptocurrency miner.
The compromised machines then expand the botnet infrastructure, conduct attacks and serve up malware like cryptocurrency miners or command-and-control servers.
“Building an attack infrastructure on top of victim machines helps conceal the attacker’s true identity and origin of the attack,” the researchers explained. “It also provides high availability infrastructure, which is very helpful when relying on compromised servers, providing infinite backup options in case one of the servers fails or loses connectivity to the internet.”
Monero is most common but Bond007.01 also mines currencies like ZCash.
The botnet is growing at a rate of around 500 new machines per day, while about the same number are delisted, the researchers said.
“This is because the vast majority of targets are not aware of security and are applying minimal to no security measures in servers,” Ziv explained. “Administrators that do respond seem to be doing this because of the spike in the CPU load rather than being aware of a ‘vulnerability’. We see many cases of reinfection, that is machines that are reinfected after being cleaned.”
That’s a mistake, GuardiCore researchers say, not only because it’s pouring money into the hacker’s coffers but because the compromised machines can easily be used for any purpose the attacker wishes.
“While organisations can treat this a minor issue of increased electric bills, with relatively simple modifications this backdoor is capable of taking complete control of thousands of victim machines, many of which contain sensitive information like mail servers,” the researchers explained. “Today’s mining may easily become a ransomware campaign, data exfiltration or lateral movement inside the victim’s network.”




