Malware targeting San Francisco transit may have been in wild at least 2 months, research shows

Ransomware used in a cyberattack that was disclosed over the weekend against San Francisco’s transit agency may be the mutated offspring of an older variant discovered by researchers in September, experts tell CyberScoop.
Morphus Labs, a Brazilian cybersecurity firm that sells both offensive and defensive software products, linked a previous incident to a hacker by the same pseudonym, Andy Saolis. The attack against the San Francisco Municipal Transportation Agency hit servers that were reportedly running on Windows 2000, an end-of-life product that is no longer officially supported by Microsoft.
“In September we worked on an incident response for a big company with subsidiaries in U.S., Brazil and India. Similar to the SFMTA case, they were infected by a ransomware that compromised machines — specifically servers — from those three different countries,” security researcher Renato Marinho of Morphus Labs told CyberScoop.
Dubbed “Mamba,” Marinho described the ransomware his team analyzed just two months ago — which shares notable similarities with the SFMTA incident — as one of the first variants to do full disk encryption by leveraging Disk Cryptor, an open-source software product.
The hacker claimed to control more than 2,112 computers — or roughly a quarter of SFMTA’s total network. The agency oversees the Muni subway system, where riders were able to see computer screens with a ransomware message.
Related research authored by TrendMicro shortly after Morphus Labs’ findings became public found that similar ransomware “not only targets resources in network shares such as drives, folders, files, printers, and serial ports via Server Message Block (SMB), but also locks the drive.”

Via Reddit user Blorq
The ransomware operators were likely able to quickly compromise a significant number of SFMTA’s machines, Marinho explained, because of how the malware collects credentials. “As soon it reaches privileged credentials from the environment, it starts to act, by fully encrypting machines’ HDs.”
“During the [previous] analysis that we made, [the ransomware] did not infect the desktop machines [like it did with SFMTA]. As such, it is possible that the previous behavior may be a kind of bug … unfortunately, all the systems that could help us with some information about the actors were encrypted as well. That time, we interacted with some other labs to look for some help regarding attribution, but found no relevant information.”
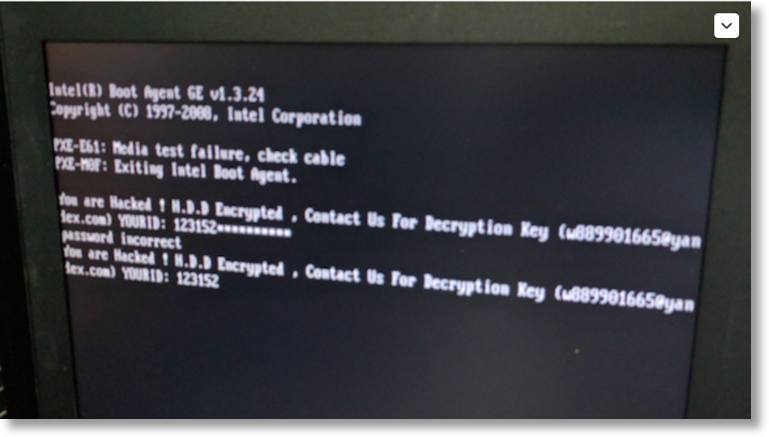
The ransom message in Morphus Labs’ cold case shares direct similarities to that used for SFMTA.
Mamba employs a 512-bit encryption key that is supported by a symmetric cryptograph algorithm called advanced encryption standard, or AES.
The encryption process behind Mamba, Marinho said, requires considerable time to deploy at scale. Meaning that if an affected machine were powered off during the encryption exercise then the victim may be able to recover files not yet locked.
“This attack used a known ransomware kit and the authors even claim it wasn’t targeted, so it doesn’t show a rise in sophistication so much as an increase in the amount of the ransom,” explained Israel Levy, a former computer security specialist in the Israel Defense Force and now CEO of security firm Bufferzone. “Attacks like this demonstrate the vulnerabilities of infrastructure and transportation networks making additional targeted attacks likely.”
An unnamed source reportedly told CBS affiliate KPIX 5 that the public transportation “system [had] been hacked for days.”
SFMTA posted an update on Sunday night concerning the incident, noting that the “situation is now contained.” The definition of contained in this context remains unclear.
“The HDDCryptor virus was first discovered earlier this year and while we have tracked a low but consistent presence within the threat landscape, we have noted a spike in the last two weeks,” said Avast Mobile Enterprise Vice President Sinan Eren. “HDDCryptor uses two legitimate tools to execute: Netpass for obtaining credentials to access network drives, and DiskCryptor to encrypt files and render them inaccessible without the ransom sum being paid.”
On Friday, SFMTA employees and riders found that company computers, email and payroll systems were held hostage. The hacker requested a ransom of roughly $73,000 in bitcoin be paid for returned access, leaving an email address, cryptom27@yandex.com, and name, Andy Saolis, in public view.
The Bitcoin Wallet address apparently used by Saolis to receive payment in the September case is different from that shared in a message over the weekend.
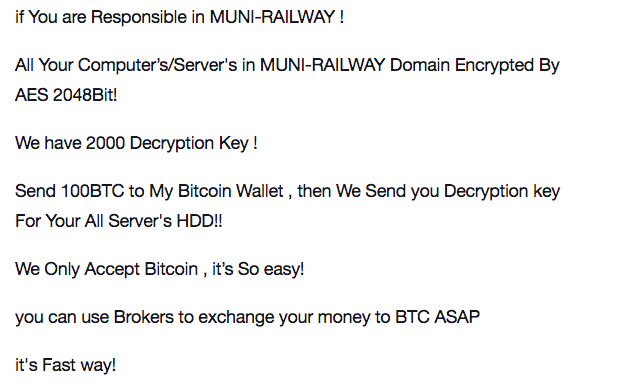
Original message from the apparent ransomware operator
“We suspect that Mamba entered in the network through a phishing e-mail,” Marinho said of the incident his team investigated in September.
Neither SFMTA nor Saolis have said how the original intrusion occurred.
“You Hacked, ALL Data Encrypted,” a message on affected SFMTA computers read.
Due to the outage, railway riders were not able to add value to their respective payment cards; pressuring SFMTA into keeping entry gates open free of charge. The financial costs of this past weekend’s security breach is believed to be significant.
“There’s no impact to the transit service, but we have opened the fare gates as a precaution to minimize customer impact,” spokesperson Paul Rose wrote in a statement. “Because this is an ongoing investigation it would not be appropriate to provide additional details at this point.”
Citing the voluntary and highly confidential nature of shared threat intelligence, a Department of Homeland Security spokesperson declined to comment on the SFMTA case.
“The correct mitigation going forward should be to update the operating system to the latest version with all patches applied and to run a robust endpoint security solution,” Eren said. “At a critical infrastructure network such the Muni one, the ideal scenario should be that all endpoint systems in the network will be backed up to a central disaster recovery solution where in case of an infection the individual systems could be restored and functionality recovered immediately.”
An FBI spokesperson told CyberScoop that the Bureau is “aware of reports regarding the MUNI ransomware hack” and is in contact with Muni officials.


