LuminosityLink malware author pleads guilty

The author of the LumunosityLink malware pleaded guilty in federal court on Monday. Colton Grubbs, a 21-year-old man from Kentucky, faced up to 25 years in prison had the case gone to trial.
LumunosityLink first earned a spotlight in 2015 when Proofpoint researchers looked past the benign advertisements for the product and found a “very aggressive key logger that injects its code in almost every running process on the computer.”
The malware was sold for $40 as a Remote Access Tool (RAT) that, according to the product’s advertising, “allows system administrators to manage a large amount of computers concurrently.” In reality, it was malware that allowed over 6,000 customersto take over thousands of computers in 78 countries.
Here was LuminosityLink’s website boasting about “powerful surveillance” capabilities:
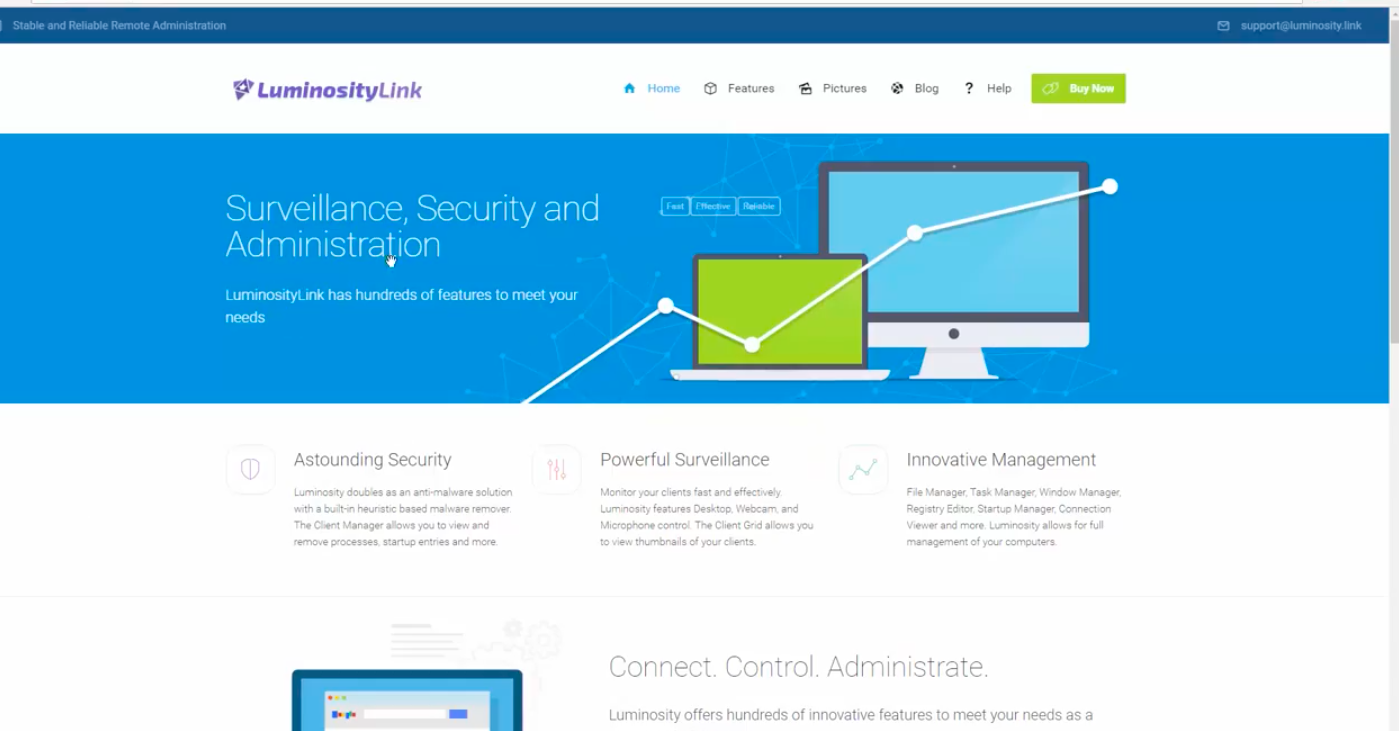
LuminosityLink was sold on HackForums, an infamous information security community that routinely features heavily in cybercrime indictments. The Mirai botnet found its way to the website in 2016 and the Blackshades RAT was infamous malware sold widely on the site before its creators were arrested.
There is a significant link between Blackshades and LuminosityLink. Both were marketed on HackForums as benign software, both were actually potent hacking tools that bestowed serious firepower on otherwise amateur actors, which led to the creators being placed in handcuffs.
Despite some of the language used to market LuminosityLink, other aspects made the tool’s intent obvious. It was marketed in the “hacking tools and programs” subforum on HackForums. The marketing emphasized the fact that the malware could be silently installed without notification and that it included key loggers and a vast suite of surveillance tools, as well as profitable cryptomining capabilities and the ability to use victims’ machines in a botnet.
Grubbs admitted to prosecutors that he knew customers used the software to illegally hack into victims’ machines.
In July, 2017, Grubbs learned of an imminent FBI raid on his apartment. He tried to hide incriminating evidence including his laptop, hard drives and a debit card used with for cryptocurrency. He also transferred 114 bitcoin from his main wallet to an array of six other wallets, a transaction worth about $273,000 at the time.
Word of Grubbs’ trouble began to spread in 2017. Europol announced action against LuminosityLink in February 2018.
You can read the plea agreement below:
[documentcloud url=”http://www.documentcloud.org/documents/4600379-2018-07-16-Plea-Agreement.html” responsive=true height=500]