New malware works only in memory, leaves no trace

A new hacking campaign identified by security researchers has struck 140 major enterprises around the world using so-called file-less malware, which injects itself into memory and leaves no trace on the hard drive — making detection difficult and attribution impossible.
Russian-based Kaspersky Lab this week published research about the new campaign, saying it had struck banks, governments and telecom companies in 40 countries, but Kaspersky didn’t give the hackers a name.
File-less malware is written directly to the victim computer’s working memory, called RAM, instead of being installed on the hard drive, where it can be discovered by security scans. The attackers employed widely used system administration and security tools — including PowerShell, Metasploit, and Mimikatz — to inject their malicious code into computer memory.
They hosted their operation on poorly controlled country code top-level domains, or ccTLDs, like those for Gabon, the Central African Republic and Mali. “The trick of using such domains is that they are free and missing WHOIS information [about who controls the domain] after domain expiration,” the researchers state.
“Given that the attackers used the Metasploit framework, standard Windows utilities and unknown domains with no WHOIS information, this makes attribution almost impossible,” they conclude.
The researchers add that the groups with the most similar tactics, techniques and procedures, or TTPs, are the banking fraud crime groups GCMAN and Carbanak.
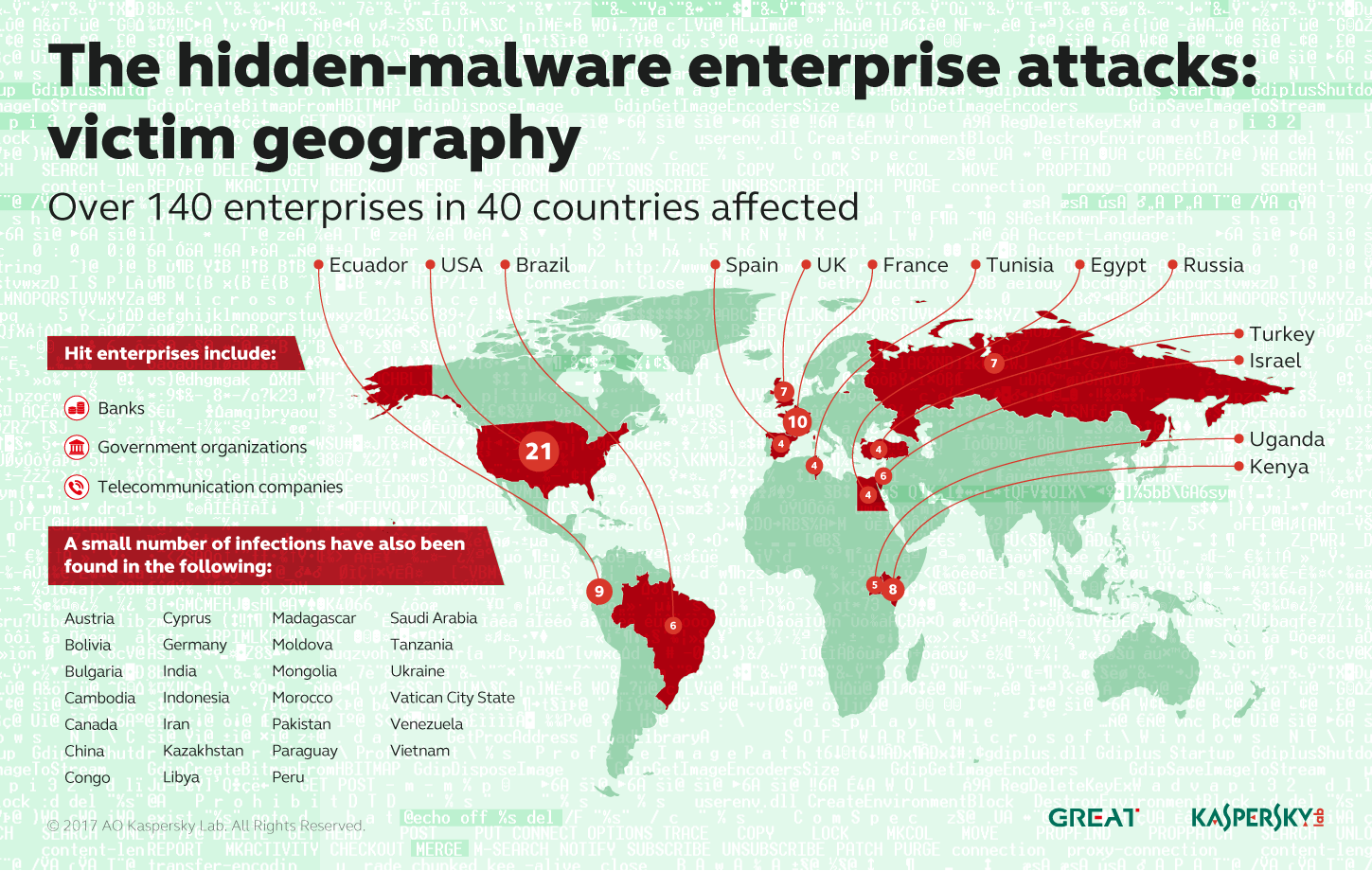
Geographical dispersion of victims of new file-less malware
The attack was first discovered last year when IT staff at a bank found code from a part of the Metasploit tool called Meterpreter in the physical memory of a Windows server. Metasploit is a widely used tool that penetration testers — hackers who attack a network to check its defenses — employ to create simulated attacks.
Kaspersky analyzed memory dumps and Windows registries from the affected machines, and were able to restore both Meterpreter and another powerful security tool called Mimikatz — allowing them to reconstruct the attack.
“These tools were used to collect passwords of system administrators and for the remote administration of infected hosts,” the researchers reported. They said the access was them used to milk ATMs.
They conclude the report by listing various traces the attackers might leave in RAM, the registry and in network traffic.
File-less malware is not new. Indeed, it was one of the tactics used by Duqu 2.0, a nation-state attacker that infested Kaspersky’s own corporate network two years ago.
What appears novel about this latest campaign is the use by financially motivated crime gangs of a technique that, until recently was the province of nation-state attackers.




