Iranian hackers have developed Mac malware, researchers say

Hackers aligned with the Iranian government have reportedly developed Mac-based malware to spy on defense contractors, according to a new report authored by security researchers Claudio Guarnieri and Collin Anderson of Security Without Borders.
The development of Mac-specific computer viruses by the hackers — known collectively as “Newscaster” or “Charming Kitten” — underscores their capability to create new espionage tools as some of their targets move to technologies beyond Windows PCs. Apple devices are commonly perceived by the public as being generally more secure.
Dubbed MacDownloader by its designers, the macOS malware agent was found lurking on a fake website designed to imitate aerospace firm United Technologies Corporation, a U.S. defense contractor that sells jet turbines, surveillance and other industrial equipment. The phony website has been previously linked by Anderson and Guarnieri to other malware staging and deployment operations.
MacDownloader has been used in campaigns that target dissidents and other Iranian activists, the report notes.
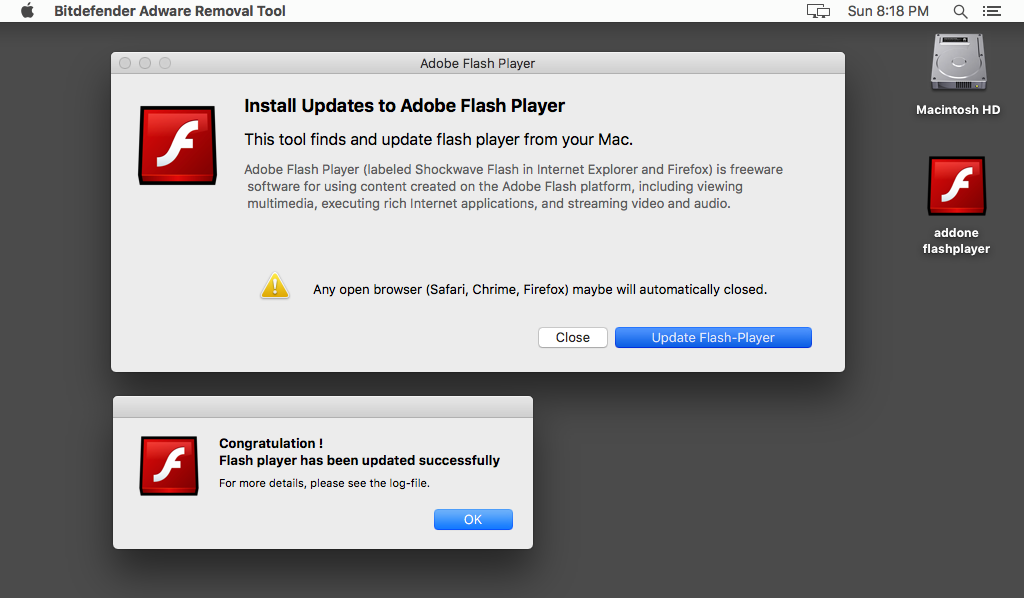
Via Security Without Borders
MacDownloader infects victims through a bogus Flash download program, which communicates with an external server where the victims’ account iCloud Keychain passwords are siphoned into. Safari and macOS’s system service will automatically save passwords in Apple’s Keychain for websites, remote file systems, encrypted drives and other assets that require user login to access.
The malware also creates defunct user login boxes to entice victims into disclosing other, relevant account information. The main purpose of MacDownloader appears to be broad reconnaissance and the acquisition of account credentials.
“The packaging of the MacDownloader sample … provides further indication of its Iranian origin through its name, ‘addone flashplayer.app,’ which would suggest that a Persian-language speaker named the file based on grammar,” the report reads. “The continuity of certain infrastructure and trends in targeting suggest a relationship to the Charming Kitten actor group, believed to based in Iran and connected to Iranian security entities.”
One of the servers linked to MacDownloader was found exposed by the researchers, enabling them to discover additional information pertaining to Newscaster’s activities, which included use of two distinct WiFi networks named Jok3r and mb_1986. Both of these WiFi networks have been named in previous Iranian hacking operations.
MacDownloader appears to have been created in late 2016 by an amateur developer; the computer virus’ code is sloppily written and some of it is lifted directly from older, exposed malware campaigns.


