Clarity needed on ‘active defense’ by cyber-victims: report

The Justice Department should issue guidance about what kinds of “active defense” measures are permissible under U.S. law and the Homeland Security Department should develop procedures for working with private sector companies that want to implement them, a report from a blue ribbon panel said Monday.
Companies experiencing cyberattacks are currently often hamstrung by a lack of clarity from U.S. federal authorities on the legality of active defense measures, states the report from George Washington University’s Center for Cyber and Homeland Security.
Active defense measures are defined as ones that fall between merely passive defense techniques like firewalls and scans at one end of the spectrum, and “hacking back” attacks like seizing control of an adversary’s server at the other end.
Active defense measures “may cross the threshold of the actor’s own network borders, and produce effects on the network of another … [impacting] the confidentiality, integrity, or accessibility of another party’s data,” states the report, produced by a 30-strong task force co-chaired by Adm. Dennis Blair, former director of national intelligence and chairman and CEO of Sasakawa Peace Foundation USA; Michael Chertoff, former secretary of Homeland Security and executive chairman and co-founder of The Chertoff Group; Nuala O’Connor, president and CEO of the Center for Democracy and Technology; and Frank Cilluffo, director of the center.
The report, its authors say, is an effort to provide a framework to help policy makers think about the legal “gray zone” of active defense measures and decide which are safe for routine use, which should only be employed sparingly and which should perhaps be ruled out, or at least only taken in close cooperation with government authorities.
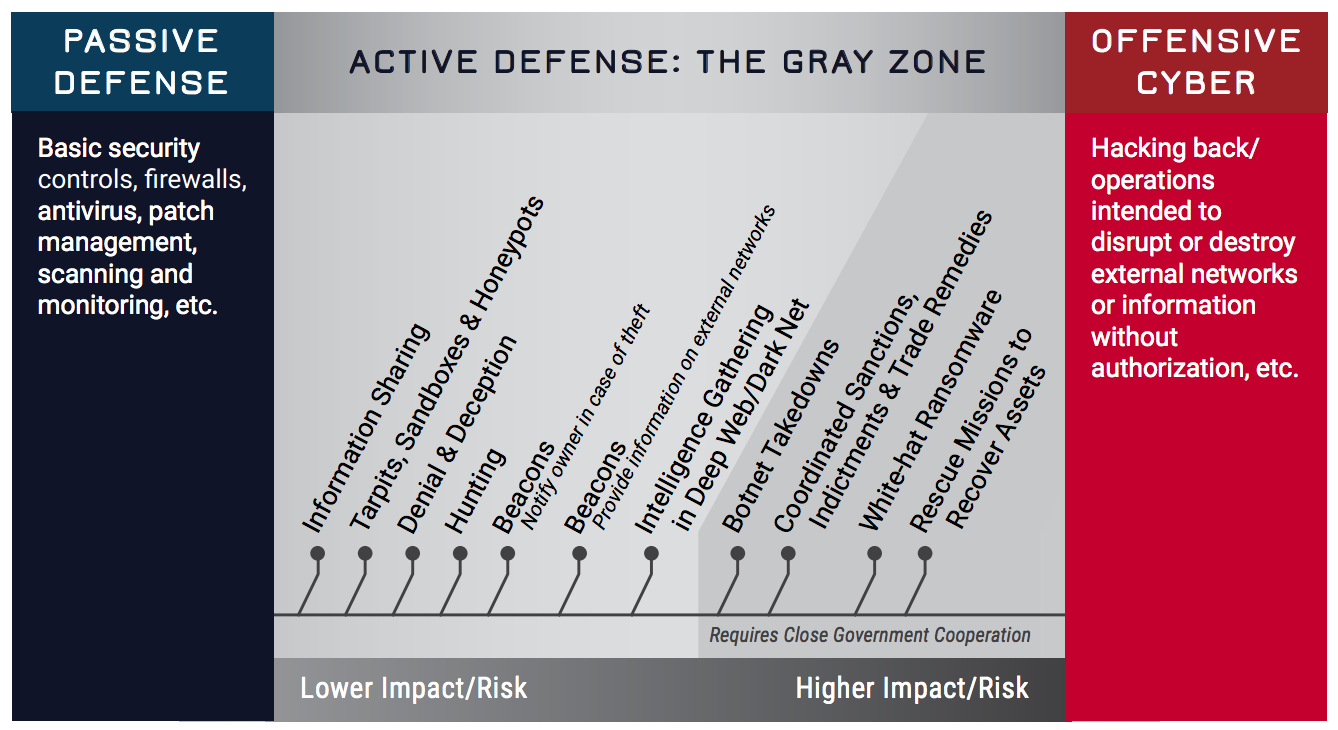
Active defense measures (source: GWU CCHS “Into the Gray”)
The authors insist that hacking back is very different from active defense and that the two terms “should not used interchangeably.”
But they acknowledge that the characterization of active defense as distinct from offense “depends upon the intent or objective of the actor implementing them. Activities aimed at securing one’s own systems, or preserving operational freedom could be characterized as defensive in nature,” even if they intrude upon another party’s networks. “Disrupting a malicious botnet, sinkholing traffic from a malicious IP address, and other activities that are taken in direct response to an ongoing threat would fall within this category,” the authors argue.
The problem, they add, is that the legal test which makes a computer intrusion a crime under the federal anti-hacking law known as the Computer Fraud and Abuse Act, is whether or not the access is “authorized.”
Because attackers are very unlikely to authorize access to their networks, the report states, “U.S. law is commonly understood to prohibit active defense measures that occur outside the victim’s own network.” An exception is when a victim company or its contractors can get permission from a third party whose network — having been hacked by the attackers — was used as a staging ground or launchpad for their operation.
In order from least risky to most risky, the report lists and defines active defense measures as follows:
- Information Sharing — The sharing of actionable cyber threat indicators, mitigation tools, and resilience strategies between defenders to improve widespread situational awareness and defensive capabilities.
- Tarpits, Sandboxes & Honeypots — Technical tools that respectively slow hackers to a halt at a network’s perimeter, test the legitimacy of untrusted code in isolated operating systems, and attract hackers to decoy, segmented servers where they can be monitored to gather intelligence on hacker behavior.
- Denial & Deception — Preventing adversaries from being able to reliably access legitimate information by mixing it with false information to sow doubt and create confusion among malicious actors.
- Hunting — Rapidly enacted procedures and technical measures that detect and surgically evict adversaries that are present in a defender’s network after having already evaded passive defenses.
- Beacons (Notification) — Pieces of software or links that have been hidden in files and send an alert to defenders if an unauthorized user attempts to remove the file from its home network.
- Beacons (Information) — Pieces of software or links that have been hidden in files and, when removed from a system without authorization, can establish a connection with and send information to a defender with details on the the structure and location of the foreign computer systems it traverses.
- Intelligence Gathering in the Deep Web/Dark Net — The use of human intelligence techniques such as covert observation, impersonation, and misrepresentation … in areas of the Internet that typically attract malicious cyber actors in order to gain intelligence on hacker motives, activities, and capabilities.
- Botnet Takedowns — Technical actions that identify and disconnect a significant number of malware-infected computers from the command and control infrastructure of the malicious network to which they’ve been recruited.
- Coordinated Sanctions, Indictments & Trade Remedies — Coordinated action between the private sector and the government to impose costs on known malicious cyber actors by freezing their assets, bringing legal charges against them, and enforcing punitive trade policies that target actors or their state sponsors.
- White-hat Ransomware — The legally authorized use of malware to encrypt files on a the computer system of a third party — like a bullet proof hosting service or cloud provider — that contains stolen information in transit to thief’s own system. Public-private partners then inform affected third parties that they have been compromised and are in possession of stolen property, which they must return in order to regain access to their files.
- Rescue Missions to Recover Assets — The use of hacking tools to infiltrate the computer networks of an adversary who has stolen information in an attempt to isolate the degree to which that information is compromised and ultimately recover it. Rarely successful.
The report also recommends that the State Department reach out to U.S. allies and work with them on “developing common standards and procedures for active defense measures,” especially because most large companies targeted by hackers operate globally, “and thus need to protect information on systems in dozens of countries.”
In addition, the Privacy and Civil Liberties Oversight Board “should carry out a review of current and proposed federal government activities related to active defense activities by the private sector, and release a public report on the results.”
Congress should “reassess language in the CFAA and the Cybersecurity Act of 2015 that constrains private sector activity on active defense, to ensure that low and medium-risk active defense measures are not directly prohibited in statute,” the authors urge.
Finally, they recommend that both Congress and the White House should enshrine the presumptive legality of active defense in law and policy.
“The framework that we provide in this report offers a sustainable path forward for responsible private sector active defense,” said center Deputy Director Christian Beckner.