Meet GreyEnergy, the newest hacking group hitting Ukraine’s power grid

Ever since the seminal cyberattacks on the Ukrainian power grid in 2015 and 2016, researchers have traced the evolution of the broad set of hackers behind the attacks in an effort to warn organizations the hackers might strike next. On Wednesday, analysts from cybersecurity company ESET added to that body of knowledge in revealing a quieter subgroup of those hackers that has targeted energy companies in Ukraine and Poland.
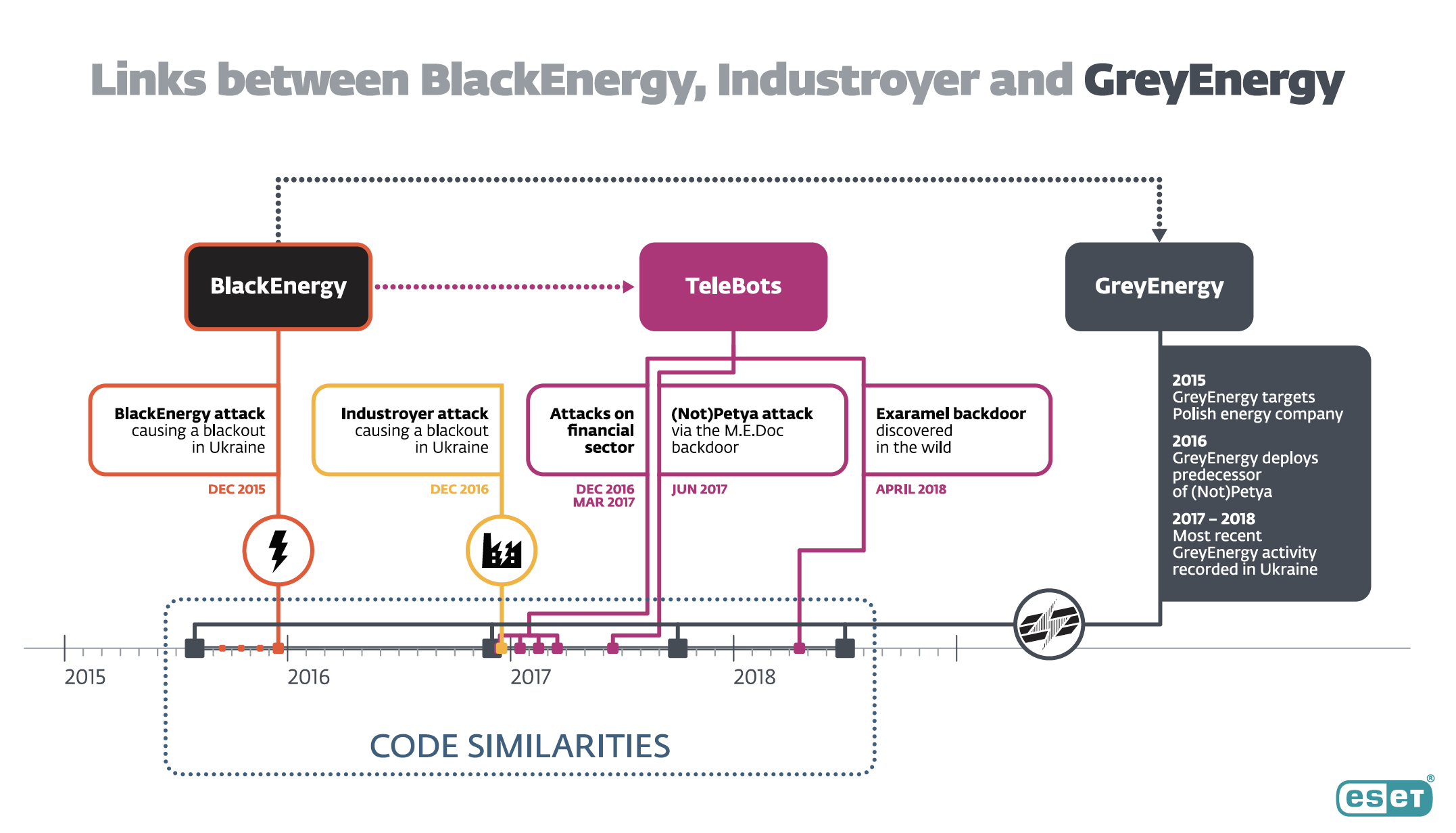
ESET has dubbed the group GreyEnergy, a derivative of the original group of hackers, which have been known as BlackEnergy. Whereas BlackEnergy is known for the disruptive 2015 attack on the Ukrainian grid that cut power for roughly 225,000 people, GreyEnergy has to date preferred reconnaissance and espionage, according to ESET. The group has taken screenshots of its possible targets, stolen credentials, and exfiltrated files.
A chart connecting Russian hacking groups. (ESET)
“Clearly, they want to fly under the radar,” said Anton Cherepanov, the company’s lead researcher on the case. ESET suspects that BlackEnergy morphed to GreyEnergy at the end of 2015, after the group grabbed the world’s attention in the first known cyberattack to cause a blackout.
Other cybersecurity companies refer to the group behind BlackEnergy as “Sandworm,” an outfit that Western governments have attributed to Russian’s military intelligence directorate. Last week, ESET researchers published evidence – in the form of custom remote access tools – that links 2015 and 2016 hacking operations against the Ukrainian grid with last year’s NotPetya malware outbreak.
“GreyEnergy is an important part of the arsenal of one of the most dangerous APT [advanced persistent threat] groups that has been terrorizing Ukraine for the past several years,” the new ESET research states, adding “we consider it to be the successor of the BlackEnergy toolkit.”
GreyEnergy’s malware has strong similarities with that of BlackEnergy and another subgroup of the hackers, known as TeleBots, that ESET says was behind the NotPetya incident. According to ESET, GreyEnergy used a “NotPetya-like worm” in December 2016, a tamer precursor to the NotPetya wiper that wreaked global havoc six months later. The worm did not spread beyond a small number of targets, causing less of a splash in the cybersecurity industry, according to ESET. But its similarities with NotPetya suggest that TeleBots and GreyEnergy have collaborated, the researchers said.
ESET researchers have not seen GreyEnergy use a malware module “capable of affecting” industrial control systems (ICS). That stands in contrast to the ICS-tailored “Industroyer” malware used in the 2016 cyberattack on a power substation in Ukraine. The GreyEnergy hackers have, however, at least once “deployed a disk-wiping component to disrupt operating processes in the affected organization and to cover their tracks,” ESET said.
In an echo of the Stuxnet attack reportedly carried out by the American and Israeli governments on an Iranian nuclear facility, GreyEnergy has apparently used a stolen digital certificate for supply-chain equipment. The certificate was lifted from Advantech, a Taiwanese manufacturer of ICS gear, according to ESET. In Stuxnet’s case, the attackers stole certificates from two hardware companies that were also Taiwanese. The new ESET research is a reminder that APTs sometimes track each other’s activity, learning from and emulating it as they see fit.



