FBI tells businesses to not pay ransomware hackers, 70 percent of US businesses do anyway

There’s no mystery as to why the ransomware epidemic is spreading so quickly in 2016: It’s a billion-dollar business.
Ransomware is a malware class that infects computers, encrypts the files and demands money in exchange for access — or the victim loses valuable data forever. The attack’s history can be traced back to 1989, but the last half-decade has seen new payment technology like bitcoin help fuel a rapid rise in ransom rates around the world. In the last year, attacks per day quadrupled, according to the Justice Department.
When businesses get hit with ransomware, they keep it a secret even as law enforcement and security experts plead for transparency and encourage them to not pay up.
And then the businesses pay the ransom 70 percent of the time anyway, according to a new study from IBM Security that looked at American-based firms. More than half of the businesses surveyed admitted they’ve already paid over $10,000 to hackers who locked up their data. A further 20 percent admitted they’ve coughed up over $40,000.
Ransomware is seen as such a large threat that businesses sometimes hold a cache of bitcoin as contingency for emergency.
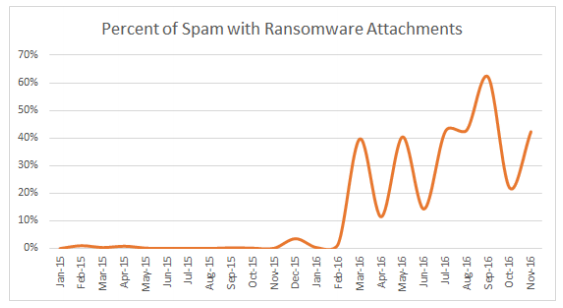
Source: IBM X-Force, 2016
Ransomware is an enormously profitable, scalable and easy trade for thieves. Experts and law enforcement forecast more infections in 2017 and ransomware is seeing a stream of innovation: A new breed was spotted in the wild just this month that incentivizes victims to infect their own friends and contacts in exchange for the key to their own data for free. Some hackers negotiate prices, others demand millions of dollars in payment.
While consumers are widely targeted, however, they’re less likely to pay up and they have less money and data to lose. It’s business targets, especially in the small and medium-sized range, that are the obvious jackpot for hackers. Most small businesses don’t offer any security training whatsoever, making them easy to strike. Almost 60 percent of all executives surveyed say they would pay ransom for lost data that included financial records, customer records, intellectual property and business plans.
Individuals pay less and are more likely to pass on the whole thing, but if a hacker hits the right target, they can get their cash. Parents are more likely to pay for access to family photos than people without children. Locking up financial data or an entire mobile device means that close to half of victims say they’re willing to pay. And although 37 percent of consumers said they’d pay over $100 in ransom, the reality shows that victims pay $500 or much higher when they actually fall prey.
The most important way to protect against ransomware is to back up data offline and to then keep it unconnected from other devices. If you have another copy of whatever is being ransomed, you don’t need to pay anything. It’s also wise to use adblockers like uBlock Origin to protect against advertising networks that have been hacked, exploited and used to infect victims on thousands of websites. Immediately applying updates to software is another crucial step that’s often avoided ostensibly in the name of convenience but undeniably at the cost of security.
Education about phishing and hacking is effective though it often feels out of the question for small businesses with less time and money to spare than their larger counterparts. But phishing remains the most used attack vector for hackers of all stripes (just ask the Clinton campaign), so it ought to be high on the priority list of any organization or individual concerned with security—and, after the year we’ve had, we should probably all be concerned.




