FBI cybercrime seizure takes down one-time Ukraine IT Army collaborator

On May 31, the U.S. Department of Justice announced that it had seized a trio of domains as part of an international cybercrime law enforcement action.
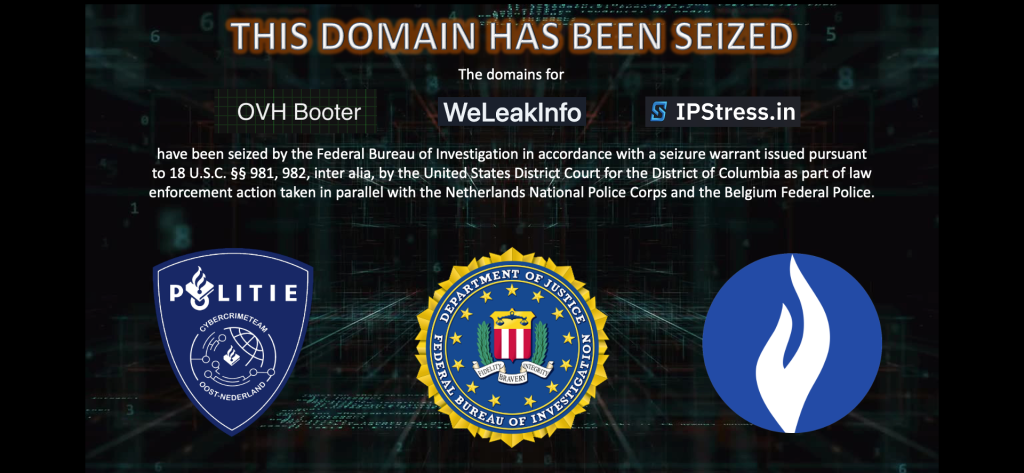
The domains — ovh-booter[.]com, weleakinfo[.]to and ipstress[.]in — enabled “two distressingly common threats,” U.S. Attorney of the District of Columbia Matthew Graves said in a statement. “Websites trafficking in stolen personal information and sites which attack and disrupt legitimate internet businesses.”
It didn’t take long for some to notice that one of the domains, IPStress, was until recently affiliated with Ukraine’s IT Army, the Ukrainian government-sanctioned but volunteer-run effort that encourages ongoing cyber attacks against a multitude of Russian targets as part of Ukraine’s efforts to defend itself against Russian military assault.
A link to the service’s website and Telegram account was active on the IT Army’s English-language site as of Tuesday but was taken down after CyberScoop inquired about the connection. Visitors to the domain are greeted with a warning that it’s been seized. Previously the site boasted “the best ip booter stresser” that “can down any game server” and was able to bypass “every protection such as cloudflare with our blazingfast methods. Buy now and enjoy the strong power from our botnets as well.”
The stated goal of the IT Army is to “create automated systems attacks on information resources and services of the enemy country.” Its website — which can be toggled between Ukrainian and English — offers various downloadable tools and instructions in order to launch distributed denial-of-service attacks on various targets, which overwhelm targeted computers and networks with traffic to render them inaccessible.
An unnamed person replying to questions sent via email to the IT Army told CyberScoop that affiliation with IPStress spanned a few weeks in May and had been “terminated … due to poor execution from their end.”
IPStress was supposed to “provide server-status services and get references on our website” in return, the person explained. The link to the site had been removed from the Ukrainian side of the IT Army’s website but not the English-language side “due to a technical issue,” the person said.
“Of course, we are not going to renew any contacts with Ipstress (sic) after the knowledge they are under FBI investigation,” the person said. “This information was new for us and we literally get to know about it from your message.”
The person added that ” the IT Army of Ukraine is a purely voluntary organization that encourages people in Ukraine to fight against Russia’s invasion in cyberspace. It is fully legal in Ukraine during war stands.”
Messages sent to the Telegram account associated with IPStress were not answered.
It’s not clear whether the site’s connection to the IT Army’s activities — which are currently legal within Ukraine but almost certainly illegal most everywhere else — had anything to do with the international law enforcement operation involving the FBI, the U.S. Department of Justice, the Netherlands Police Corps and the Belgian Federal Police.
In a statement issued June 1, Belgian officials said a man in his 20s was arrested May 31 in connection with “having launched, or allowed to launch computer attacks against various interests in Belgium and abroad,” according to a Google translation. The statement said the investigation took a year and followed on a previous investigation into a site that resold stolen passwords and usernames in large quantities.
Both Belgian agencies declined to share any additional details including detained man’s name or any attorneys involved in the case.
The FBI and U.S. Department of Justice announced in January 2020 that it had seized “weleakinfo[.]com” as part of an international law enforcement operation involving the United Kingdom, Netherlands, Germany and Northern Ireland. The June 1 Belgian statement noted that a spin-off for weleakinfo, hosted on servers in the Netherlands, came online three days after the original went down.
The FBI and the the U.S. Attorney’s Office in D.C. declined to comment. Requests for comment sent to the Netherlands Ministry of Justice and Security were not answered. A spokesperson for the Ukrainian Ministry of Digital Transformation said the “ministry doesn’t represent [IT Army]” but that “we are partners and have the one enemy.”
The spokesperson did not respond to additional questions about whether the Ukrainian government was aware of the FBI actions, either before or after the announced seizure.
The Russian government has incessantly bombarded Ukrainian targets with cyberattacks for years, with spillover effects impacting the other countries multiple times. Both in the days and weeks before the Feb. 24 Russian military assault and ever since, Ukrainian government officials have repeatedly detailed a litany of Russian-linked cyberattacks ranging from insignificant website defacements to wiper attacks that have destroyed data to a sophisticated attack on satellite communications as the Russian military advanced.
Multiple governments formally blamed Russia for the satellite cyberattack and condemned the actions in coordinated statements released May 10.

This story was featured in CyberScoop Special Report: War in Ukraine




