That was fast: Thousands of computers now compromised with leaked NSA tools, researchers say

Thousands of Microsoft Windows machines worldwide are infected with an NSA-developed backdoor that hackers installed by reusing leaked executable code from an outdated hacking toolkit belonging to the spy agency, multiple security researchers tell CyberScoop.
The mysterious Shadow Brokers group published a package of internal NSA documents last week, containing among other things the computer code for a series of exploits, implants and other hacking tools. In the days since the leak first became public, hackers have mulled over the trove and begun reverse-engineering and recycling some of the capabilities, CyberScoop previously reported.
One of these hacking tools, a backdoor implant codenamed DOUBLEPULSAR — which is used to run malicious code on an already compromised box — has already been installed on 30,000 to 50,000 hosts, according to Phobos Group founder Dan Tentler. Other researchers have also engineered different detection scripts to quickly scan the internet for infected computers.
John Matherly, the CEO of internet scanning-tool maker Shodan.io, said that upwards of 100,000 computers could be affected.
“Shodan has currently indexed more than 2 million IPs running a public SMB service on port 445. 0.04 percent of SMB services that we’re observing in our data firehose are susceptible to DOUBLEPULSAR which results in a projection of ~100,000 devices on the Internet that are impacted,” Matherly wrote in an email. “Shodan has already indexed 45k confirmed [infections] so far.”
Machines owned by data storage providers Enzu and Psychz Networks have been hardest hit with the implant, according to information collected using Shodan.io.
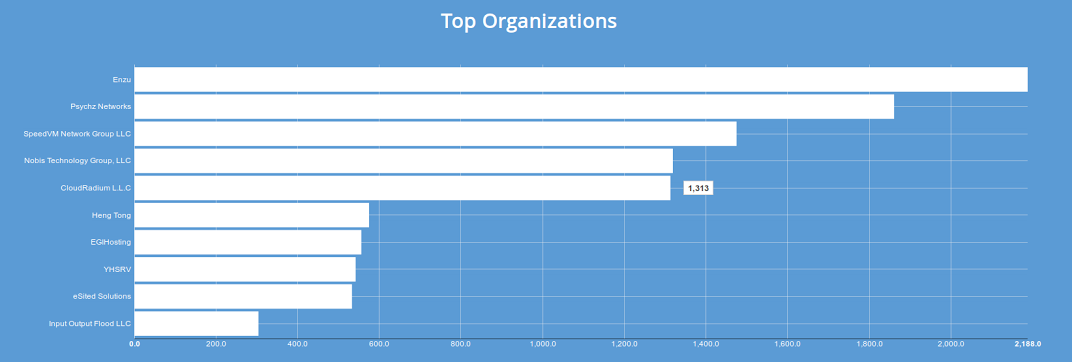
graphic provided by Shodan.io
The findings are significant because they illustrate, among other things, the rapid pace at which cybercriminals can effectively adopt and then launch cyberattacks with complex, NSA-grade weaponry. Additionally, the prominence of DOUBLEPULSAR underlines the fact that numerous computers were already vulnerable to intrusion.
A scan on April 18, independently conducted by security firm Below0Day, collected data for 10 hours and found a total of 35,000 computers hit with DOUBLEPULSAR, said co-founders Jason Leitner and Vladimir Vlaski. The vast majority of affected systems were located inside in the U.S., the firm found.
“DOUBLEPULSAR is basically a loading dock for extra malware. Its purpose is to communicate over the [Microsoft Server Message Block] port, listen for traffic and receive and execute shellcode or DLL that an attacker will send it. It doesn’t open a new port, it doesn’t write anything to disk, it sits in memory and it listens,” explained Tentler. “If it is installed, you can then give it instructions, run this DLL for me, it will run it and you can pop Metasploit shells or Empire or Puppy or Pedalcheap, which is the NSA toolkit.”
In theory, hackers could leverage other capabilities in the leaked NSA toolkit to breach a machine, which is necessary before installing the backdoor. In addition to DOUBLEPULSAR, the material published by the Shadow Brokers offered two tools, respectively codenamed ETERNALBLUE and FUZZBUNCH, which can be used to launch an exploit effective against older versions of Microsoft operating systems, including Windows XP, Vista and Server 2008 R2.
Tutorials for how to use both FUZZBUNCH and ETERNALBLUE are available in underground hacking forums and have been circulating on the deep web since April 14, CyberScoop previously reported.
Once installed, DOUBLEPULSAR is a stealthy backdoor that’s difficult to detect and continuously relays new information back to its controller. Organizations already infected with the implant will be continuously open to hackers.
While Microsoft already released a security patch for a majority of the exploited vulnerabilities in affected operating systems, it remains unclear how many individual machines applied the software update, globally. More than 65 percent of desktop computers connected to the internet last month ran on older versions of Windows like Vista, according to estimates from the tracking firm Net Market Share.
The sheer number of computers infected with DOUBLEPULSAR is likely the work of amateurish hackers, experts said.
“The presence of DOUBLEPULSAR doesn’t mean they’re infected by the NSA, it means there is a loading dock ready and waiting for whatever malware anyone wants to give it,” Tentler said. “The chances are none that all theses hosts [were hacked by] the NSA. It is effectively trivial to go compromise all these hosts with the flick of a wrist.”
He continued, “if you’re smart, you install DOUBLEPULSAR , install whatever malware you want and if you’re smart, you remove DOUBLEPULSAR because then no one else can get at your malware. If you’re a smart bad guy that’s what you should be doing.”
Patrick Howell O’Neill contributed to this report.




