Fake Christmas Eve termination notices used as phishing lures

A phishing campaign using a well-known malware families is employing a pair of particularly devious methods to trick targets into opening an infected file: fake employee termination notices and phony omicron-variant exposure warnings.
A threat researcher going by the name of “TheAnalyst” posted a screenshot of the fake employment termination notice Dec. 22, attributing it to a Dridex affiliate.
The suspicious email told the target that their employment would cease as of Dec. 24, and that the decision was not reversible. An attached password-protected Excel file promised additional details.
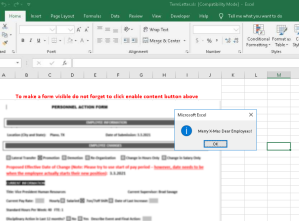
Once a recipient opened a file, a blurred form appeared with a button to “Enable Content,” which enabled the file to run an automated script through its macros feature, a technique intended to help automation that simultaneously has been abused for years for malicious purposes. After the button was clicked, a pop-up window appeared: “Merry X-Mas Dear Employees!”
Dridex is a trojan dating back to 2014 that typically spreads through email phishing campaigns and is associated with credential theft. It’s been used to steal more than $100 million from financial institutions and banks spread across 40 countries, according to the U.S. Treasury Department.
Meanwhile, according to Bleeping Computer, which first reported the campaign Tuesday, the Dridex malware would be downloaded to the victim’s computer from a Discord server, and begin stealing credentials.
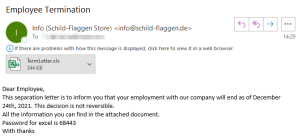
Phony termination notice sent to targets Dec. 22.
Dridex is believed to have been developed by a Russian hacking group known as Evil Corp., one of the most notorious and prolific cybercrime groups in recent years. The U.S. government sanctioned the group in December 2019, and also indicted its alleged leaders, Maksim Yakubets and Igor Turashev, for their role in developing Bugat, the precursor malware to Dridex.
A reply to TheAnalyst’s tweet containing the phony termination notice noted that in some versions of the email, the “Merry X-Mas” pop-up substituted racial slurs instead of the word “Employees.”
The racist messaging with this particular Dridex effort dates back a couple months, TheAnalyst told CyberScoop Thursday. A phishing email sent to targets around Black Friday, for instance, referenced killing “black protesters,” with a license. “If you find this message inappropriate or offensive, do not hesitate to click complaint button in the attached document and we will never contact you again,” the message read.
The hackers also infuse racist email addresses into the malware payloads, TheAnalyst said, as an effort to troll researchers. Targets of the campaigns don’t see this part of the campaign, but researchers who seek out, examine and expose phishing campaigns do.
A separate Dridex-laced email in the same campaign was also sent to targets on Tuesday.
This one came with the subject line: “Positive OMICRON results,” and warned the target that they’d been exposed to a coworker who tested positive for the the omicron variant of COVID-19 sometime between Dec. 17 and 19. “All the information you can find in the attached document,” the email read, adding a password for the file. The pop-up message associated with this document displayed what purported to be a COVID-19 funeral assistance phone line.

