New fileless malware uses DNS to pull down instructions

A new, very stealthy malware variant uses the internet’s address directory to covertly pull down commands from its authors, which then are directly implemented by victimized computers — leaving no trace on the hard drive for digital detectives to analyze.
DNSMessenger, as the malware’s been dubbed by threat researchers at Talos Group, was initially discovered by a researcher with the Twitter handle @simpo13. He tweeted at Talos about his discovery after discovering that the source code of a portion of the malware contained a character string that decoded as: “SourceFireSux.” SourceFire was the original name of one of the components of the Talos Group, which is now part of Cisco.
The DNS or domain name system looks up a written website address like www.cyberscoop.com and translates it into a numeric internet protocol (IP) address that takes a web browser or other application to the correct internet server.
DNSMessenger is a remote access tool, or RAT — malware that enables an attacker to take control of an infected machine. Talos researchers highlighted the malware’s exceptional stealth, attributing it to “an attacker who has taken significant measures to avoid detection.”
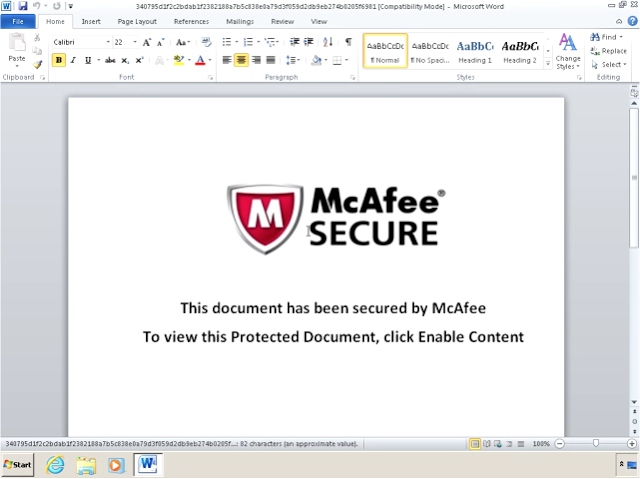
Malicious word document from DNSMessenger malware (source: Talos)
The malware arrives in a specially engineered word document, disguised as an attachment, and the victim is prompted to “click enable content,” with the promise that “This document is secured by McAfee.”
“This is likely an effective way to increase the odds of the victim opening the file and enabling macros as McAfee is a well known security vendor and likely immediately trusted by the victim,” write the researchers.
Once opened and enabled, the document launches a Visual Basic for Applications macro that starts a PowerShell session. The VBA script also reaches out out to a command and control server via DNS, importing new commands for each stage of the PowerShell attack.
There are no files written onto the target machine’s hard drives and most enterprises don’t monitor or filter DNS queries so the malware is capable of operating completely under the radar.
“This is an extremely uncommon and evasive way of administering a RAT,” wrote researchers Edmund Brumaghin and Colin Grady. “It also illustrates the importance that in addition to inspecting and filtering network protocols such as HTTP/HTTPS, SMTP/POP3, etc. DNS traffic within corporate networks should also be considered a channel that an attacker can use to implement a fully functional, bidirectional C2 infrastructure.”
Their blog post gives no information about who might have been attacked with DNSMessenger.
“We don’t have a ton on the initial vector,” said Craig Williams, senior technical leader and global outreach manager for Cisco Talos, in an email to CyberScoop. “It’s fairly targeted.”




