Russia-linked hackers impersonate NATO in attempt to hack Romanian government

An elite hacking group linked to the Russian government masqueraded as a NATO representative to send a barrage of phishing emails to diplomatic organizations in Europe, including Romania’s Foreign Ministry of Affairs, documents show.
CyberScoop obtained a copy of one such phishing email that researchers have attributed to the hacking group, which is known as APT28 or Fancy Bear. The email, which carries a booby-trapped attachment that leverages two recently disclosed Microsoft Word vulnerabilities, shows that the government-backed hacking group effectively spoofed a NATO email address to make the message appear authentic. The hq.nato.intl domain is currently used by NATO employees.
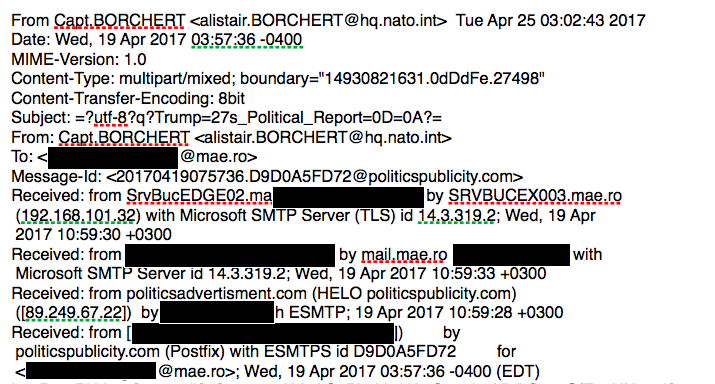
Code in email sample obtained by CyberScoop. Email address and IP of victim is censored.
The file has already been submitted to Virus Total, a publicly maintained library of computer viruses. Typically files don’t appear on the site unless they have been found in the wild.
An analyst from cybersecurity firm FireEye confirmed the phishing email pictured above is in fact authentic and related to APT28 activity. Initially it was not publicly known who was targeted as part of this campaign or what the senders’ full address was. APT28 has been cited as the possible source of attacks on the campaign of French presidential candidate Emmanuel Macron.
NATO would not comment on this specific attack, but said hackers target the alliance’s systems constantly.
“We are aware that such attacks include the use of spoofed NATO email addresses,” a NATO official told CyberScoop. “As is common practice, whenever we detect spoofed email addresses, NATO alerts the responsible authorities in Allied countries to prevent attacks from spreading. The hacker group APT 28 – which is also called Fancy Bear or Pawn Storm – is well known to the cyber defense community and we track its activities closely.”
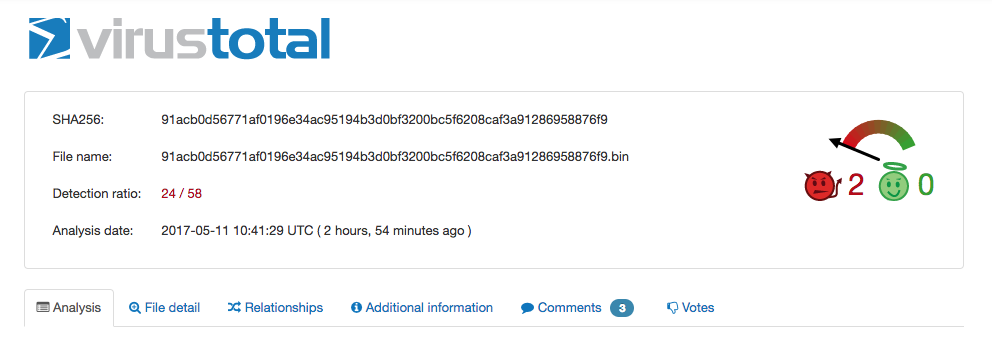
The malicious file has already been uploaded to VirusTotal — meaning that at least one target is aware of the attack.
One related phishing email sent to Romania’s Foreign Ministry of Affairs contained an attachment named “Trump’s_Attack_on_Syria_English.docx,” which served up a news article in Microsoft Word, researchers told CyberScoop. If this attachment is opened on a vulnerable system it will also covertly download a remote access trojan by exploiting two coding flaws in Word that until recently were considered zero-day vulnerabilities. Microsoft patched them Tuesday.
Romania’s Foreign Ministry did not respond to CyberScoop’s request for comment.
The malware is downloaded locally, meaning that it does not require an internet connection. Dubbed “GameFish” by FireEye, the remote access trojan used in this case is a known hacking tool of APT 28 that provides attackers with a wide range of espionage capabilities including data exfiltration and lateral network movement.
FireEye analyst Ben Read told CyberScoop the tool could be used to uploaded other computer viruses on an already compromised machine.

subject body message of email
An analysis of the phishing email sent to the Romanian government office suggests that the victims were using antivirus products developed by IronPort and Sophos. Unfortunately, it appears that neither product successfully labeled the attachment as malicious in this case.
It remains unclear exactly how many organizations were targeted or successfully infected by APT28’s Trump-themed phishing scheme, said Read, who broadly defined the campaign as “narrow” in scope.
An IP address (89.249.67.22) connected to multiple phishing samples links back to a command-and-control infrastructure used by APT28 that was originally exposed more than five months ago by the security community. The reuse of an already uncovered attack server surprised some researchers, and they said it illustrates the emboldened nature of Russia’s offensive cybersecurity efforts.
“Despite including a coveted zero-day exploit in their attack, APT28 failed to implement proper operational security by brazenly re-using attack infrastructure publicly uncovered by security researchers in late 2016,” said Javier Castro, director of security research for U.S.-based Area 1 Security.
FireEye and another cybersecurity firm, ESET, both published extensive technical reports Tuesday concerning the aforementioned political espionage campaign. The reports did not disclose information concerning sender data or potential victims.
While FireEye originally found evidence in April that APT28 was using two valuable Microsoft Word exploits, researchers waited until the company issued a patch Tuesday before sharing their findings publicly.
APT28 has been actively involved in political espionage operations across Europe for the better part of 10 years. In 2016 the clandestine unit gained mainstream publicity after hacking into the Democratic National Committee and email inbox of top Democratic political strategist John Podesta.
A report authored by the Office of the Director of National Intelligence claimed in January that APT28 is the work of Russian intelligence forces.




