Report: U.S. military can’t guarantee retaliation against major cyber attack

For at least the next decade, cyber superpowers Russia and China will have the capability to launch devastating online attacks against U.S. vital industries like banking and telecommunication, that will “far exceed” any ability of the U.S. military to defend against, Pentagon science advisors say in a new report.
Worse, concludes the “Final Report of the Defense Science Board Task Force on Cyber Deterrence,” published this week, the U.S. military itself has a “deep and extensive dependence on information technology as well” — making it vulnerable to cyberattacks that might thwart an American response to such an online assault.
Without assured retaliation capability, the U.S. cannot effectively deter cyber strikes, a situation that “threatens to place the United States in an untenable strategic position,” the report states.
As a result, the task force recommends the Pentagon must create a cyber-resilient second-strike capability that it calls a “thin line” element — to ensure it can strike back even after a massive surprise cyber attack and effectively “underwrite deterrence of major attacks by major powers.”
Even regional powers like Iran and North Korea “have a growing potential to use indigenous or purchased cyber tools to conduct catastrophic attacks on U.S. critical infrastructure.”
U.S. authorities must “work with the private sector to intensify efforts to defend and boost the cyber resilience of U.S. critical infrastructure” so as to reduce this vulnerability to second-order cyber attacks by rogue nations. “It is no more palatable to allow the United States to be held hostage to catastrophic attack via cyber weapons by such actors than via nuclear weapons.”
Third and finally, the report states, “a range of state and non-state actors have the capacity for persistent cyber attacks and costly cyber intrusions against the United States, which individually may be inconsequential … but which cumulatively subject the nation to a “death by 1,000 hacks.'”
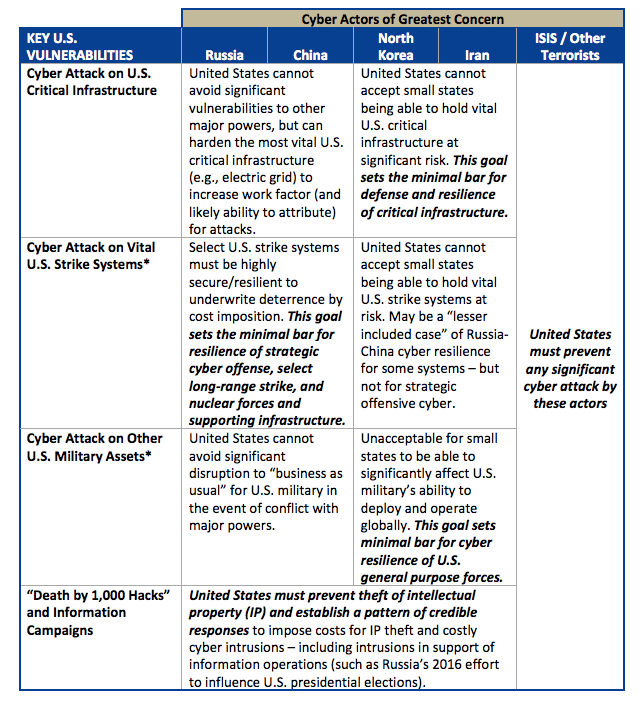
Setting the Bar for Cyber Resilience to Underwrite Cyber Deterrence (Source: DSB)
In addition to developing a “thin line” cyber-resilient second-strike capacity, the report recommends two other national lines of effort in cybersecurity.
U.S. military planning should “tailor” its deterrence posture against the full range of potential attacks that could be conducted by each category of potential adversary. “And it must do so [so as to be effective] in contexts ranging from peacetime to ‘gray zone’ [or hybrid warfare] conflicts to crisis to war … One size will not fit all.”
And the nation as a whole has to work to improve what the science board calls “foundational capabilities” like attribution of cyber attacks; cyber-resilience of critical infrastructure for the military, civilian government and private sector; and “innovative technologies that can enhance the cybersecurity of the most vital U.S. critical infrastructure.”
The task force was established in 2014. It is co-chaired by James Gosler of the Johns Hopkins University Applied Physics Laboratory and former Department of Defense cyber policy official James Miller. The membership reads like a who’s who of cyber expertise and scholarship, including Jason Healey of Columbia University, Martin Libicki of the Naval War College and former NSA Deputy Director Chris Inglis.




