The Dark Overlord was recruiting employees and looking for attention before 9/11 data dump

Months before The Dark Overlord claimed it stole a trove of sensitive documents about the 9/11 terrorist attacks, the hacking group was struggling to live up to its own reputation.
The hackers were perhaps best known for a two-year cybercrime spree in which they took credit for leaking unaired episodes of the Netflix series “Orange is the New Black,” then for harassing U.S. schools and sending death threats to students in 2017. Both incidents generated international media attention, but it wasn’t long before authorities were on the case, with Serbian police arresting a suspected member in May 2018.
While The Dark Overlord denies one of its members was apprehended, the group took steps to staff up in the months that followed. A new report from the threat intelligence provider Digital Shadows, prepared exclusively for CyberScoop, indicates that the hacking group sought new members and methods of gaining publicity.
“Do YOU want to get Rich? Come work for us!,” The Dark Overlord wrote in a Nov. 14, 2018, thread on KickAss Forum, a cybercriminal marketplace on the dark web that charges for entry.
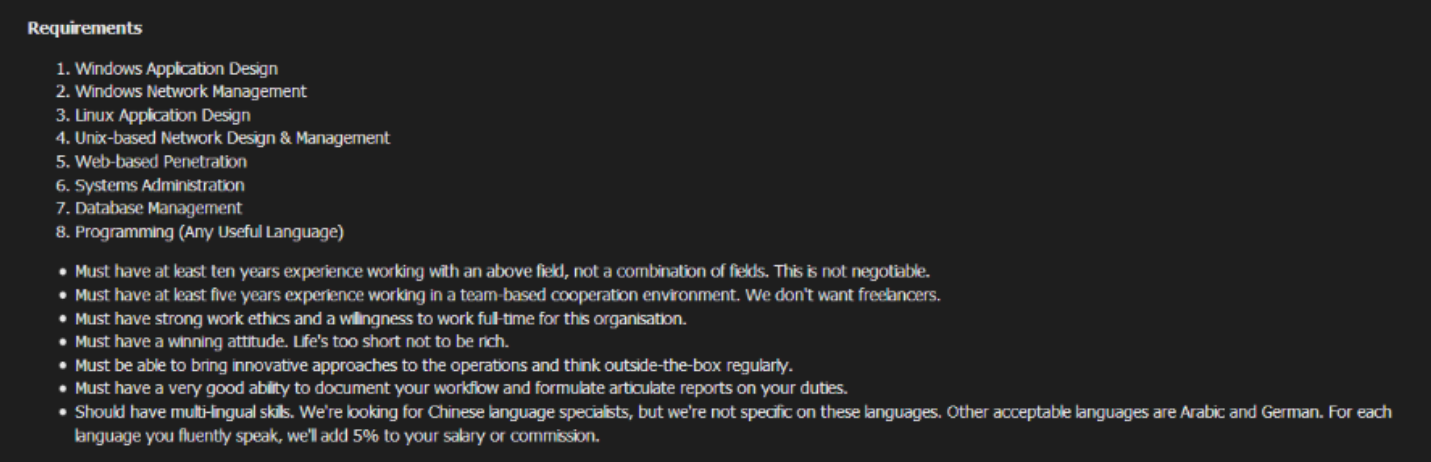
The Dark Overlord’s recruitment campaign initially aimed to fill four vacancies, and the group later said three positions had been filled, according to Digital Shadows. Job requirements included experience with Windows, Linux as well as expertise in Unix-based design and network management and penetration testing. New employees would be paid 50,000 pounds ($63,500) monthly, plus add-ons and a likely pay bump up to 70,000 pounds ($89,000) monthly after two years.
“You’ll be working in a strong team-based environment, communicating and collaborating with like-minded and ambitious individuals,” says the job posting. “You’ll be checking into project trackers, accepting suitable workflow positions, and carefully documenting your work for review. You’ll be engaged in operations against various companies and governments and world-wide deployments. If you’re goal-oriented and used to objectives and achieving them, then you’re perfect for us.”
“Must have a winning attitude,” the ad says later. “Life’s too short not to be rich.”
The Dark Overlord did not respond to a request for comment before press time.
 A job description posted by The Dark Overlord on the KickAss hacking forum last year. Click to enlarge. (provided by Digital Shadows).
A job description posted by The Dark Overlord on the KickAss hacking forum last year. Click to enlarge. (provided by Digital Shadows).
The group also has advertised multiple directories of hacked files on KickAss before the forum was rendered inaccessible on Jan. 4, according to Digital Shadows. One gaming database contained 131,000 records, while another contained 67,000 medical records.
Last month, the group was promising data from a Bahamas-based bakery and a perfumery based in Monaco, researchers found. The Dark Overlord said it had access to point-of-sale machine data, corporate bank accounts and customer credit card information stolen from both companies.
In another message from early December, The Dark Overlord challenged other forum members to find a SQL injection vulnerability in the Wall Street Journal’s website, a flaw that could allow attackers to access sensitive information without the news outlet’s knowledge. Another user calling himself “NSA” replied that he had found the bug. The Dark Overlord congratulated NSA, but no other information was available in the thread, Digital Shadows said.
Then, the hacker group made more noise than it has since 2017. On New Year’s Eve, The Dark Overlord claimed it had breached a law firm to uncover documents that would yield new information about the 9/11 attacks.
In a thread on KickAss, then in since-removed posts on PasteBin and on Twitter, The DarkOverlord claimed it had stolen emails, retainer agreements, nondisclosure agreements, litigation strategies, liability analysis and other information that would embarrass high-profile insurers Lloyd’s of London and Hiscox Syndicates as well as Silverstein Properties, a New York real estate firm. All three firms denied being hacked, though Hiscox confirmed to Motherboard a law firm that advised the company had experienced a breach.
The Dark Overlord announced it would publish the stolen material in five data dumps that would go live only after escalating payment goals, from $5,000 worth of bitcoin to $2 million, had been met. The first installment of the “9/11 Files” was released last week, consisting mostly of legal memos assessing the legal liability for various airlines and companies following the 2001 attacks.
The group’s drip-drip approach, combined with the it’s work to create media headlines, is influenced by the Shadow Brokers, a group of suspected Russian hackers who published U.S. National Security Agency hacking tools in 2016 following a similar auction on the social media site Steemit.
“There are very close similarities between TDO’s tactics and that of theshadowbrokers (one of the last hacking groups with genuine capabilities that garnered widespread media attention),” wrote Rafael Amado, a Digital Shadows strategy and research analyst, in the report, adding that the tactics “can also be taken as an indication the group are crying out for attention by mimicking tried and tested publicity techniques.”
“TDO are consciously imitating theshadowbrokers pricing and PR models: releasing information in small batches, opting for public crowdfunding, and following theshadowbrokers to the Steemit platform (we should note that whereas theshadowbrokers have over a thousand followers, TDO has fewer than 50).”




