Costa Rican president begins tenure with ransomware national emergency declaration

The new president of Costa Rica declared a national emergency over the weekend as fallout continues from a late-April ransomware attack.
President Rodrigo Chaves Robles, who began a four-year term as president Sunday after winning the country’s April 4 election, signed the declaration on May 8 as one of his first official acts, according to local news outlet Amelia Rueda. The executive decree reads, in part, that Costa Rica is “suffering from cybercriminals, cyberterrorists” and that the decree allows “our society to respond to these attacks as criminal acts.”
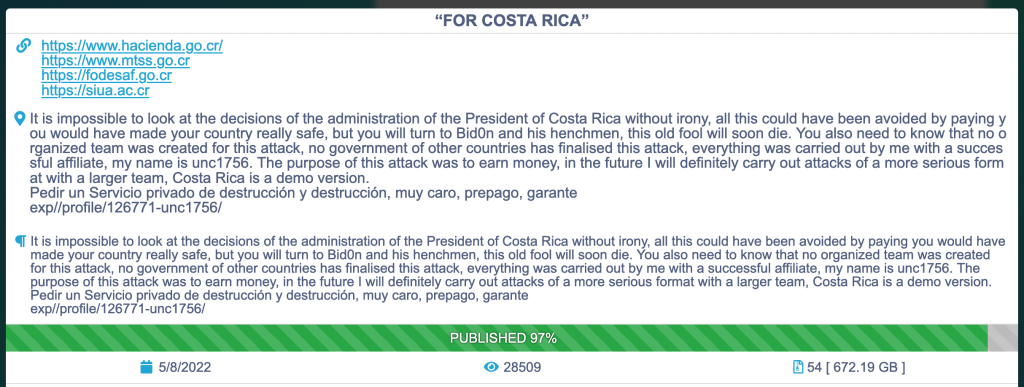
Somebody calling themselves “unc1756” using the Russian-based Conti ransomware platform claimed responsibility for the April 17 attacks in a post on the Conti dark web data portal. The post indicates that 97% of the stolen data has been published so far, totaling more than 672 gigabytes of information.
The post also blames the government of Costa Rica for not paying the original $10 million ransomware demand, which outgoing President Carlos Alvarado said was an attempt to “threaten the country’s stability in a transitional situation.”
The hacker message reads: “It is impossible to look at the decisions of the administration of the President of Costa Rica without irony … All this could have been avoided by paying you would have made your country really safe, but you will turn to Bid0n (sic) and his henchmen, this old fool will soon die.” The poster went on to say the purpose of the attack was “to earn money” and “in the future I will definitely carry out attacks of a more serious format with a larger team, Costa Rica is a demo version.”
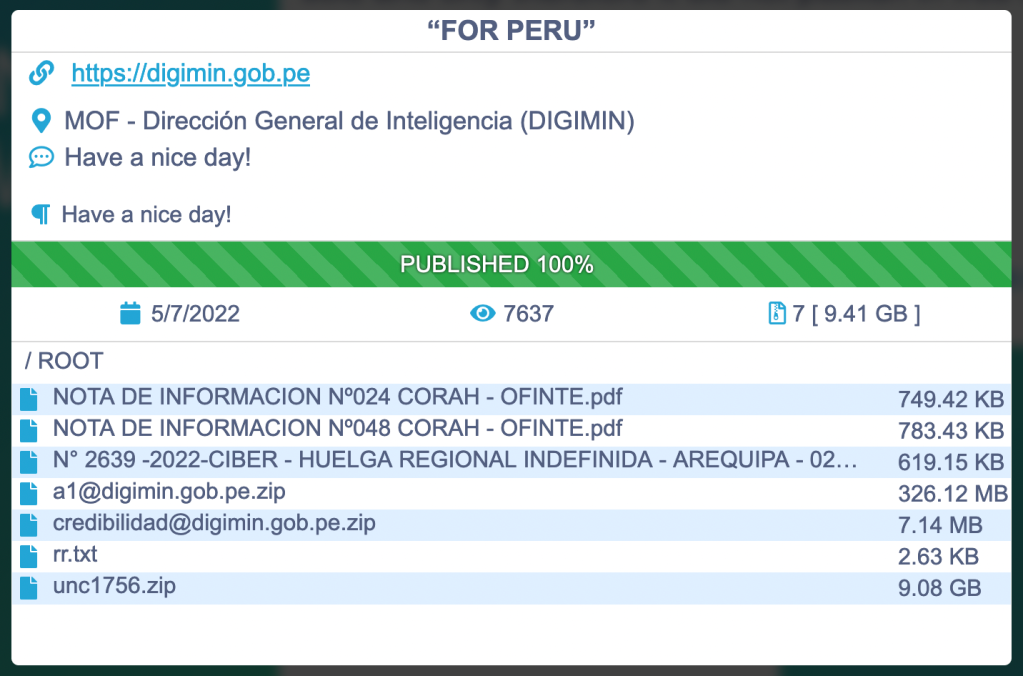
Shortly after the Costa Rica attacks, nearly 9.5 gigabytes of data taken from Peru’s intelligence agency were posted to the Conti leak site. One of the file names in that dump referenced “unc1756,” but it’s not clear if the same people were behind both attacks.
The term “UNC” in information security circles sometimes refers to uncategorized clusters of threat activity.
The U.S. State Department announced a $10 million reward for information leading to the identification and/or location of anybody holding a “key leadership position” within the Conti organization May 6, two days before the Costa Rican emergency decree. An additional $5 million reward is available for information leading to the arrest and/or conviction of anybody taking part in a Conti ransomware incident.
A State Department spokesperson told CyberScoop Monday that the “United States remains committed to protecting all potential ransomware victims around the world from the exploitation of cyber criminals,” and that if offered the rewards in conjunction with Costa Rica.
“Announcing this reward jointly with the Costa Rican government signals the commitment of the United States to support its allies against the leaders and affiliates of the Conti ransomware variant group.”
State Department spokesperson
Conti-related ransomware attacks have left more than 1,000 victims in their wake since the first reported Conti ransomware incident in the U.S. in July 2020, generating an estimated $150 million in victim payouts through January 2022, according to the FBI.
“Announcing this reward jointly with the Costa Rican government signals the commitment of the United States to support its allies against the leaders and affiliates of the Conti ransomware variant group,” the State spokesperson said, noting that the U.S. government is looking “to other partner nations willing to bring justice for those victim businesses and organizations affected by ransomware incidents.”
Conti operates like other ransomware groups in that a core group of developers maintain and update the source code and operate the online data portal while “affiliates” carry out the attacks and split the proceeds with the developers.
The group seems to have deep connections within Russia, but is made up of people from multiple countries. On Feb. 25, the day after the Russian invasion of Ukraine, a message posted to the group’s site pledged support for the Russian government. Shortly after that a Ukrainian researcher with insider access posted troves of the group’s internal data, revealing a highly organized structure. The group weathered the incident and kept on much as it did before.
Also last week, the Department of Transportation’s Pipeline and Hazardous Materials Safety Administration proposed a $986,000 fine for Colonial Pipeline in response to what the agency says were several federal pipeline safety regulations during inspections between January and November 2020. Some of the violations may have contributed to the company’s handling of its pipelines in the wake of the May 2021 DarkSide ransomware attack, the agency said in a statement. DarkSide, like Conti, has been linked to Russia.
A Colonial Pipeline spokesperson told CyberScoop Monday that the agency’s notice was “the first step in a multi-step regulatory process and we look forward to engaging with PHMSA to resolve these matters.” The spokesperson said the company’s coordination with government was “timely, efficient and effective,” and said the company hopes that the timing of the announcement “does not overshadow the important work being done collaboratively by industry and government to address these threats and protect our critical infrastructure.”
Updated, 5/9/22: To include a statement from Colonial Pipeline.




