This elite cybercrime group is wreaking havoc on the U.S. restaurant industry

A sophisticated hacking group with suspected ties to cybercrime gangs operating in Eastern Europe is now actively targeting and breaching prominent brand-name restaurants in the U.S.
A recently disclosed data breach suffered by the Chipotle chain was carried out by hackers linked to a group known as FIN7 or Carbanak Group, CyberScoop has learned. In addition to Chipotle, the hackers appears to be targeting national restaurant franchises Baja Fresh and Ruby Tuesday, according to malware samples and other evidence CyberScoop obtained.
More than 20 U.S.-based hospitality companies — the sector that includes hotels and restaurants — have been successfully hacked by FIN7 since the summer of 2016, two cybersecurity researchers told CyberScoop on the condition of anonymity in order to speak freely regarding ongoing investigations.
On Feb. 22, a phishing email carrying an attachment titled “Payment overdue.eml” was sent to an email account associated with a Chipotle location in Tulsa, Oklahoma. The body of the phishing email describes a nonexistent overdue payment and encourages the victim to open a booby-trapped attachment. The email sender is listed as Michael Smith, an imaginary manager for a nonexistent company named Slazzer LLC.
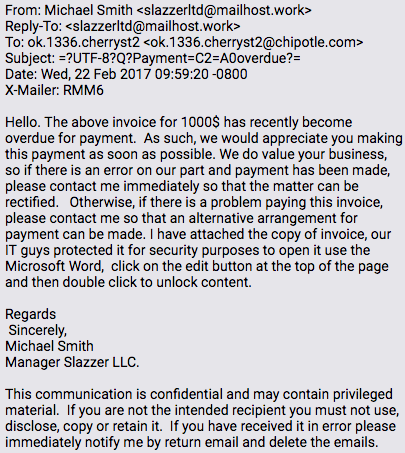
Original Chipotle phishing email
The malware-laden attachment in the email sent to the Tulsa-based Chipotle is a malicious Microsoft Office .RTF file with an embedded OLE object. The file was registered on VirusTotal on Feb. 22.
It’s believed the attackers themselves scanned the file on that date to test its effectiveness against antivirus products. A forensic analysis of the malicious code shows correlating evidence to support a connection between the sender and FIN7’s past escapades already identified by private sector cybersecurity firms.
In early January, cybersecurity researchers for Tr1adx identified a similar phishing email to the one listed above and also attributed it to hackers associated with FIN7. It’s believed this phishing campaign is expansive and has impacted hospitality businesses across not only the U.S., but also in Australia, Ireland, England, Switzerland and the Bahamas.
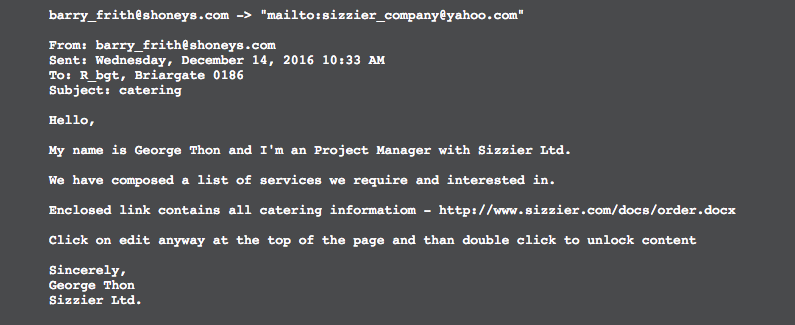
Research conducted by Tr1adx
“This highly targeted phishing attack appears to have targeted a user at the restaurant in order to limit the effectiveness of corporate security initiatives,” said Blake Darché, co-founder of cybersecurity firm Area 1 Security, which specializes in helping enterprises defend against phishing emails. “Only preemptive action across the full technology stack can stop targeted phishing attacks. Legacy spam-focused email defenses continue to let these highly targeted attacks proliferate across corporate networks.”
Two other related file samples were also detected on VirusTotal in the last month. Those files are titled “Order bajafresh.docx” and “Order Ruby Tuesday .rtf,” which indicates that Baja Fresh and Ruby Tuesday were likely targeted. Once again, the files carry signatures and other indicators that are characteristic to FIN7.
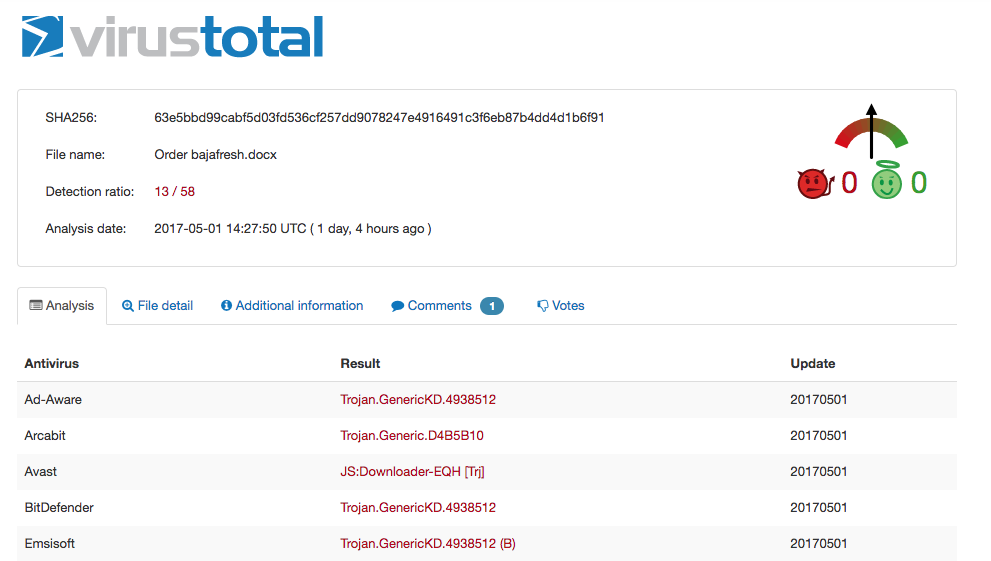
File designed to target Baja Fresh carries many of the same indicators for the Chipotle sample.
It remains unclear whether Baja Fresh or Ruby Tuesday were hacked or simply targeted.
Spokespeople for Baja Fresh did not respond to CyberScoop’s inquiry concerning the evidence of an attempt against its networks. Spokespeople for Ruby Tuesday were contacted, but did not provide comment by time of publication. Chipotle’s Chief Financial Officer Jack Hartung said that the company “will refrain from providing additional commentary” regarding the hacked payment processing system.
It remains possible that FIN7 was not the only hacking group with access to Chipotle systems.
Chipotle first acknowledged the breach during an earnings call on April 25. An investigation by law enforcement in tandem with private sector incident response firm Mandiant is ongoing. The fast-casual chain said it believes the unauthorized activity was contained to between March 24 and April 18, beginning about one month after the aforementioned phishing email file was first detected by VirusTotal.
FIN7 typically relies on well-crafted phishing emails and malicious websites that serve malware to initially breach individual storefronts in order to steal credit card and other payment information that is commonly saved on a shared corporate infrastructure. The hacking group is one of the most prolific cybercrime syndicates in the world and accounts for a significant percentage of all payment system breaches in recent years.
“Carbanak has been especially active recently,” said Darché. “This successful [Chipotle] breach demonstrates just how effective Carbanak is even when compared to nation state actors such as the Duke’s or Duqu.”
FIN7 is an amorphous entity with likely various offshoot teams, researchers say. While the group’s signature backdoor implant and command and control infrastructure is unique and not accessible to other hackers, several other tools they’ve employed are used by other criminals.
Notably, the group is financially motivated in nature, often targeting organizations with a high volume of payment transactions, based on research conducted by cybersecurity firms FireEye, Kaspersky Lab and TrustWave. The group’s past activity is not believed to be espionage related or driven by the national security interests of any specific foreign government.




