DHS briefs industry on shift in Chinese hacking that ‘increases the risk for all of us’

U.S. officials on Wednesday continued to warn industry about the threat posed by Chinese government-backed hackers by detailing how those teams have evolved and urging companies to better secure IT services that can be an avenue for stealing proprietary data.
“Their strategies have shifted from labor-intensive, one-off compromises of individual targets to the use of the force-multiplier effects that enable them to compromise multiple targets through a single attack,” Rex Booth, a Department of Homeland Security cyber official, said during a webinar presentation to the private sector. “That shift in strategies increases the risk for all of us.”
The public webinar focused on APT10, a group tied to China’s civilian intelligence agency, the Ministry of State Security. Analysts say the MSS has supplanted the People’s Liberation Army to become Beijing’s preferred arm for conducting economic espionage.
U.S. officials and security researchers say APT10 has targeted the “managed service providers” that corporations use for IT configuration, exploiting that access to scope the networks of data-rich companies.
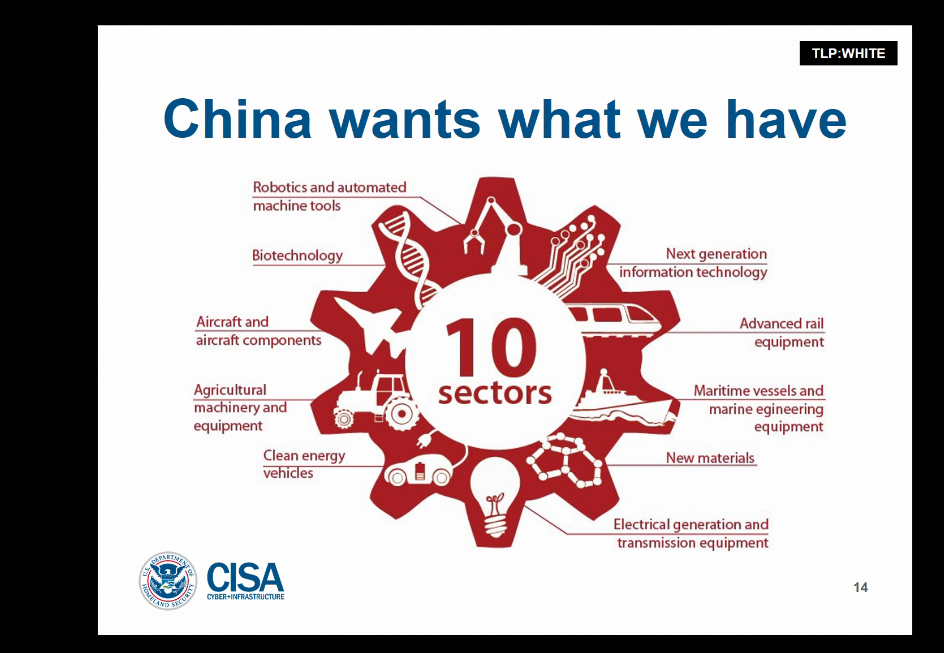
A slide from the DHS presentation.
“This type of activity has the potential to be used much more widely to affect millions more internet users around the globe,” said Chris Krebs, head of DHS’s Cybersecurity and Infrastructure Security Agency.
Booth said that while DHS had seen a downturn in activity from APT10 since the Department of Justice announced charges against two of its alleged operatives in December, “That doesn’t mean we should drop our guard.”
Beijing’s alleged economic espionage is directly tied to the Chinese government’s five-year strategic plans, Booth said. “Those plans read like a blueprint for the likely targets of Chinese espionage.” The Chinese government has denied allegations it uses hacking to steal corporate data.
The briefing came hours after cybersecurity companies Recorded Future and Rapid7 revealed a 2017-18 cyber-espionage campaign that APT10 allegedly conducted against a European software provider, American law firm, and a global apparel company.
By making more forensics on APT10’s operations public, government and corporate officials are trying to prevent future breaches. Eoin Miller, an analyst at Rapid7, advised organizations to carefully review attempts to communicate with their VPN providers from unusual networks or countries.
DHS analysts echoed that advice during the webinar, and offered a mix of technical mitigations and general warnings.
“[O]ur underlying message here is: you can outsource your operations, but you cannot outsource your risk,” Krebs said.
The DHS briefing is part of a broader pressure campaign that the Trump administration is putting on Beijing to curtail its alleged sponsorship of hacking and espionage operations to steal U.S. intellectual property.
“We are now making it clear to China that after years of targeting our industries, and stealing our intellectual property, the theft of American jobs and wealth has come to an end,” President Donald Trump said in his State of the Union address Tuesday.




