China’s vulnerability disclosure system twice as fast as U.S. version

China’s National Vulnerability Database works more than twice as fast on average than its U.S. counterpart, according to new research.
On average, U.S.-CERT takes 33 days after the public disclosure of a software vulnerability to complete the cataloging process and create an entry in the National Vulnerability Database (NVD), whereas China’s version (CNNVD) is updated an average of just 13 days after public disclosure, according to research published by cybersecurity firm Recorded Future.
In its posting, the firm analyzed two years of vulnerability reporting data from both NVD and CNNVD.
NVD was created in an effort to build an authoritative database of confirmed vulnerabilities in software. U.S. and other cybersecurity professionals use it as a checklist, to find out when software their organization is using might be vulnerable to hackers. Any delay between the disclosure of a vulnerability and its publication in NVD represents a risk for cybersecurity because organizations might be unaware of vulnerabilities in their systems which might be exploited by hackers. If CNNVD is beating NVD to the punch, then Chinese companies will in theory be better protected than their U.S. competitors.
Because averages can be distorted by a small number of outlying data points (in this case, very long delays in vulnerability cataloguing) Recorded Future analyzed the data based on percentiles as well. “Within six days of initial disclosure, 75 percent of all vulnerabilities published on the web are covered in CNNVD. The U.S. NVD takes 20 days,” the researchers write. “CNNVD captures 90 percent of all vulnerabilities within 18 days. The NVD takes 92 [days].”
Even in cases where the disclosure is coordinated — and publicly released only after being reported to NVD — the Chinese lag only a median of one day behind their U.S. counterparts. “When the vendor doesn’t tightly coordinate with NVD, it takes NVD 38 days to report on 75 percent of published vulnerabilities and 125 days to cover 90 percent.” For CNNVD in these cases those figures are seven days to 75 percent and 23 days to 90 percent.
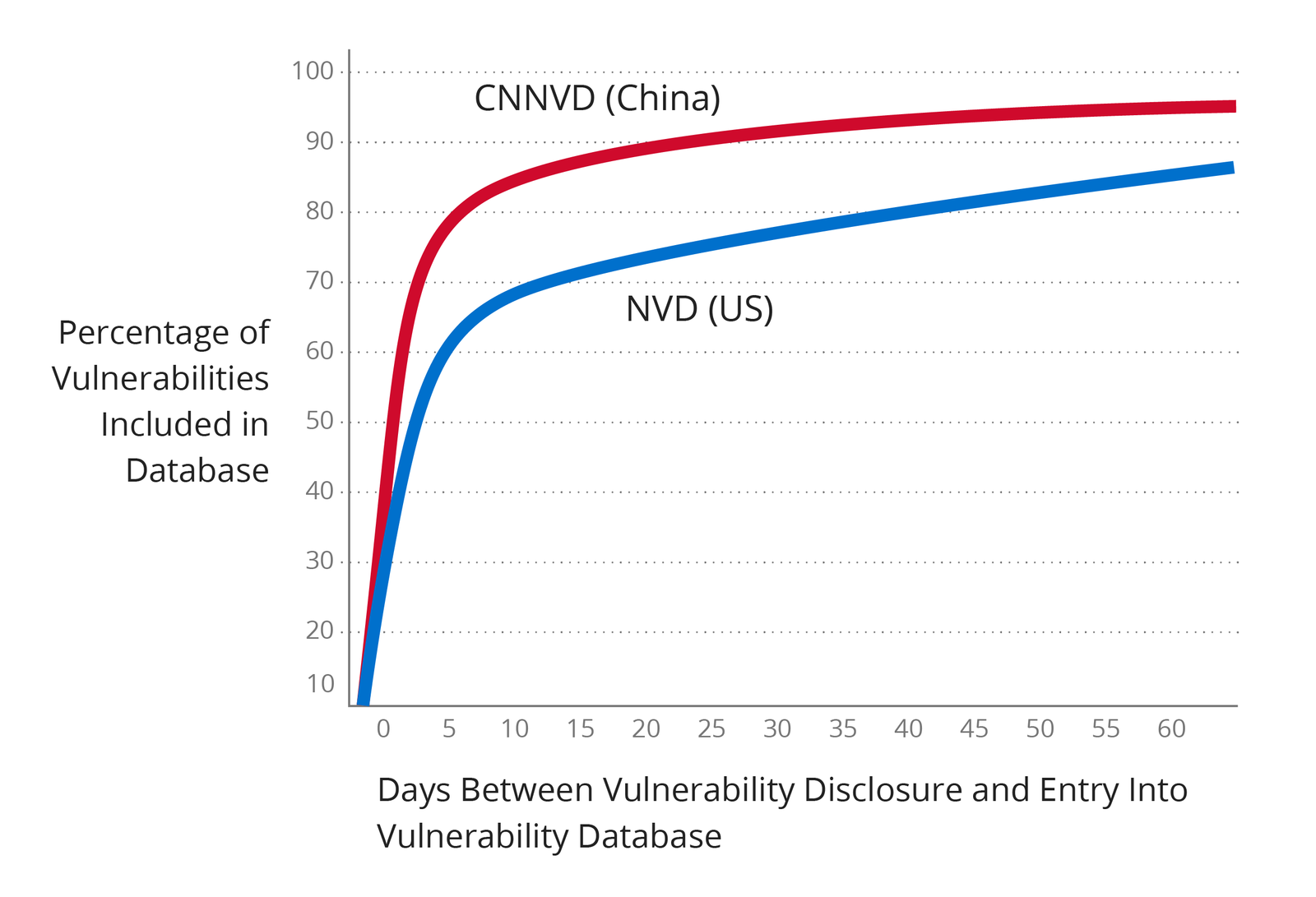
Vulnerability reporting delays for Chinese and U.S. National Vulnerability Databases (Source: Recorded Future)
The analysis concludes that this large gap is because CNNVD proactively scours the web and other sources of information, looking for vulnerability information, whereas NVD waits for reports from vendors to be processed through the Common Vulnerabilities and Exposures (CVE) database maintained by The MITRE Corporation.
“The NVD performs analysis on CVEs that have been published to the CVE Dictionary,” according to the NVD website.
“China has prioritized timely disclosure by using extensive sources of vulnerability information across the web rather than relying on voluntary industry submissions,” the researchers find, accusing the U.S. system of being too process orientated.
“NVD publication delays of weeks and months occur because NIST and MITRE are waiting for the voluntary submissions of the vendors … associated with the vulnerabilities,” concludes the research, “MITRE manages the process, but doesn’t enforce timely submissions to the CVE Dictionary. NVD uses the CVE Dictionary as its sole source. The end result is that there is no U.S. government ‘comprehensive cybersecurity vulnerability database.'”