Chinese hackers targeted U.S. political reporters just ahead of Jan. 6 attack, researchers say

Hackers connected with the Chinese government engaged in numerous phishing campaigns targeting U.S.-based journalists since early 2021, with operations focused on political and national security reporters and White House correspondents in the days leading up to the Jan. 6 attack on the Capitol, researchers said Thursday.
The previously unreported efforts are just a few examples of the digital risks that reporters and media companies are facing from an array of well-resourced state-backed hackers doing everything from gathering information to spreading malware.
Researchers with cybersecurity firm Proofpoint shared the details Thursday as part of a report looking at these kinds of operations carried out by China, Iran, North Korea and Turkey. The attacks both targeted journalists and had hackers posing as journalists to target others, the researchers said.
Journalists and media organizations face the same cyberthreats as any other sector, the researchers noted. But given the nature of the work journalists do, they make especially juicy targets for government hackers.
“The media sector and those that work within it can open doors that others cannot,” the researchers wrote. “A well-timed, successful attack on a journalist’s email account could provide insights into sensitive, budding stories and source identification.”
And posing as journalists allows hackers the ability to “spread disinformation or pro-state propaganda, provide disinformation during times of war or pandemic, or be used to influence a politically charged atmosphere,” the researchers added.
Attacks on journalists’ professional email accounts is the most frequent way these kinds of operations take place, given that journalists are frequently communicating with unknown parties, the researchers said.
Overall, the data presented in Thursday’s report suggests that “some campaigns have targeted the media for a competitive intelligence edge while others have targeted journalists immediately following their coverage painting a regime in a poor light or as a means to spread disinformation or propaganda,” the researchers wrote.
Cyberattacks on journalists and media organizations are nothing new. In 2013, The New York Times reported that Chinese hackers had been persistently attacking the paper over the course of several months in connection with reporting on then Chinese Prime Minister Wen Jiabao. In February of this year, The Wall Street Journal reported that hackers likely associated with China hacked and accessed emails and other documents of journalists and other employees in an intelligence collection effort.
And in November, the Department of Justice alleged that two Iranian hackers accessed the computer network of a media company with aims to modify content on news organizations’ websites as part of a sprawling election interference operation.
China
Chinese hackers associated with what are believed to be two distinct campaigns targeted U.S.-based journalists over the course of 2021 and into 2022, the researchers said. The first group, tracked by Proofpoint as TA412 but by Microsoft as Zirconium, used malicious emails with web beacons to collect information from targets’ systems spanning several months in early 2021.
The researchers identified five campaigns, “most notably those covering U.S. politics and national security during events that gained international attention.” The researchers recorded “a very abrupt shift in targeting of reconnaissance phishing” in the days immediately preceding the January 6 attacks on the U.S. Capitol, the researchers said, with “a focus on Washington DC and White House correspondents during this time.”
Emails sent to targets used subject lines pulled from recent articles, while the body of the email duplicated the text from those articles. Also included in the body was a PNG image file that connected to a hacker-controlled domain, a campaign identifier, victim identifier, campaign date and information about the image file.
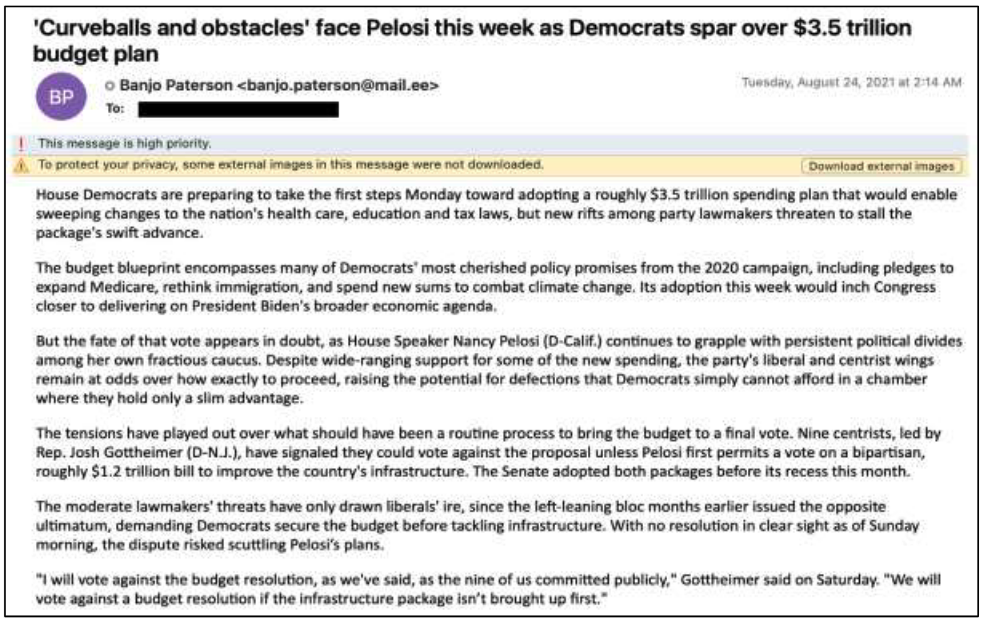
In August, after months-long break, the same group resumed attacks, but broadened the target pool to include “those working on cybersecurity, surveillance, and privacy issues with a focus on China.” There was another pause, and then the attacks resumed in February 2022, the researchers said.
A separate Chinese group, tracked by Proofpoint as TA459, targeted victims with a malicious document that, if opened, installed and executed Chinoxy malware. The malware gives an attacker a backdoor to a victim’s computer and allows them to maintain persistence, the researchers said.
North Korea
A North Korean campaign tracked by Proofpoint as TA404, known by others as Lazarus, “in early 2022 targeted a U.S.-based media organization with job opportunity-themed phishing,” the researchers said, after the unnamed organization published a story critical of North Korean leader Kim Jong Un.
The Proofpoint researchers note that they did not see the follow-up emails associated with this campaign, but noted that Google’s Threat Analysis Group published findings in March on a similar North Korean operation that shared the same indicators of compromise.
Turkey
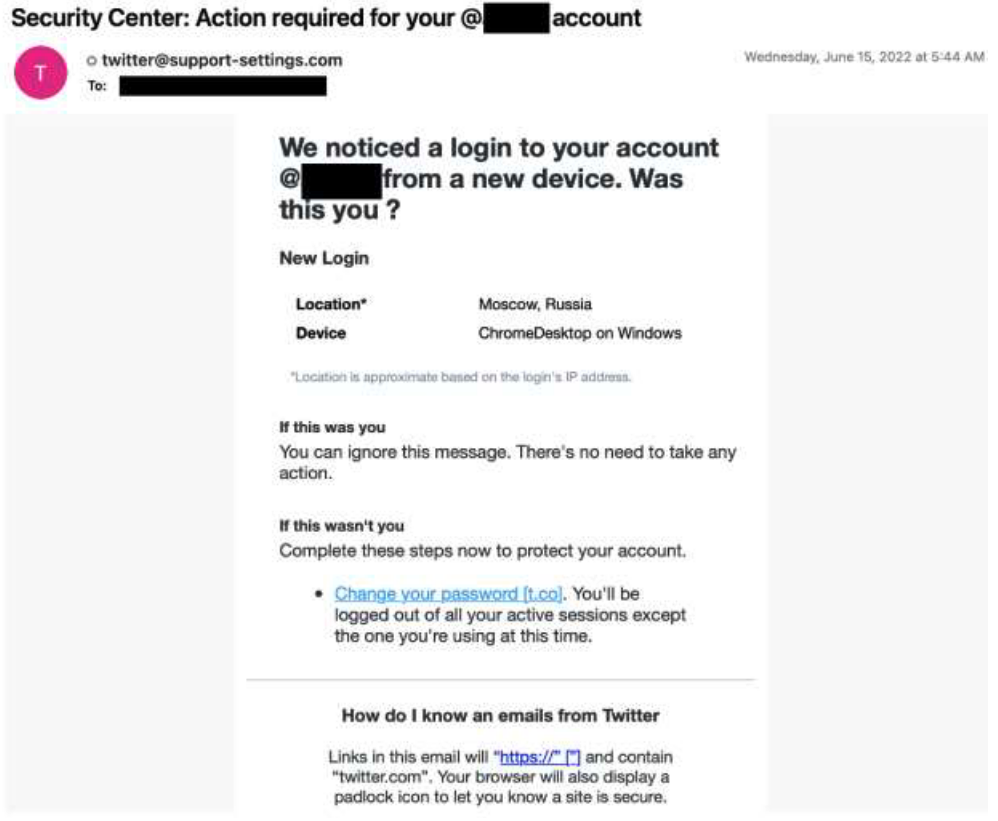
A group Proofpoint tracks as TA482 and associates with the Turkish government has been “regularly engaging in credential harvesting campaigns” aimed at taking control of social media accounts associated with mostly U.S.-based journalists and media organizations, the researchers said.
Twitter credentials for journalists “from well-known news outlets to those writing for an academic institution” were targeted as recently as June, the researchers said, with phony Twitter security login pages.
Iran
An Iranian group the researchers call TA453, also known as Charming Kitten, “routinely masquerades as journalists from around the world,” the researchers noted. The hackers use the personas to engage targets in benign conversation before deploying credential harvesting malware.
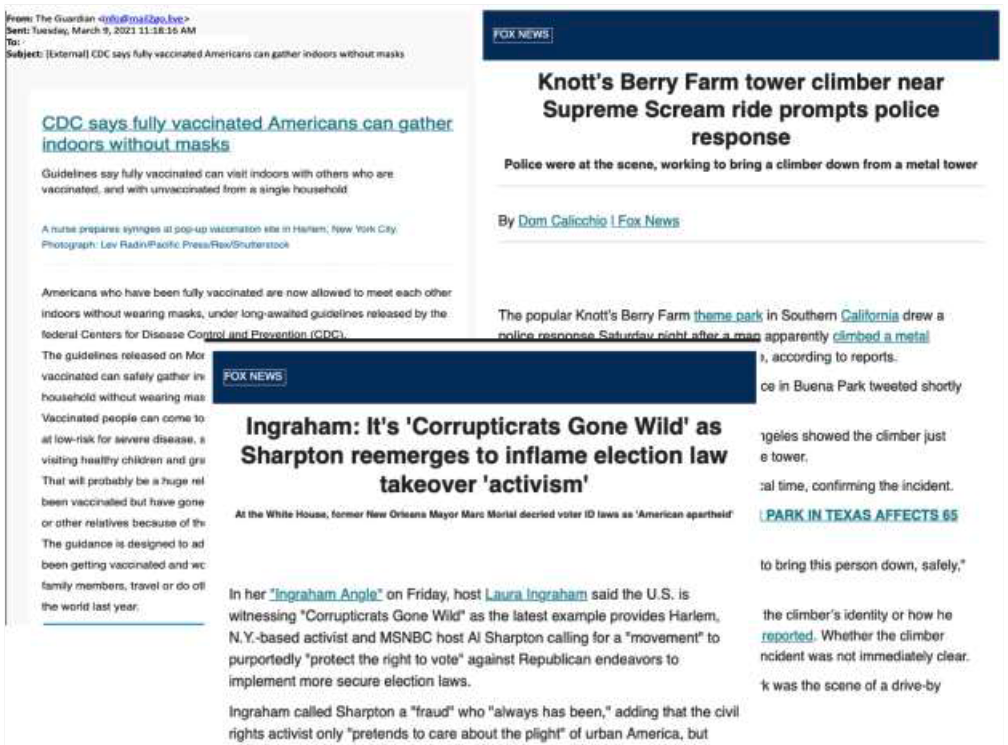
A separate Iranian group, TA456 or Tortoiseshell, also acts as media organizations and routinely send newsletters purporting to be news from across the political spectrum, including Fox News and The Guardian. The activity likely complements previous campaigns targeting defense contractors, the researchers said, which Proofpoint reported in July 2021.
And a third Iranian group, tracked by Proofpoint as TA457, masquerades as “iNews Reporter to deliver malware to public relations personnel for companies in the U.S., Israel and Saudi Arabia, the researchers said. A March 2022 effort sent an email with the subject “Iran Cyber War,” while others have included Iran, Russia, drones, war crimes, “secret weapons” and more.
Proofpoint identified campaigns from this group every two to three weeks between September 2021 and March 2022, the researchers said.
“The varied approaches by APT actors — using web beacons for reconnaissance, credential
harvesting, and sending malware to gain a foothold in a recipient’s network — means those
operating in the media space need to stay vigilant,” the researchers concluded.
Journalists and media organizations reporting on China or North Korea “may become part of their collection requirements in the future,” they said.




