Cellebrite can now unlock iPhone 6 and 6+, also extract data from array of popular apps

Cellebrite, the Israel-based firm that makes millions selling smartphone cracking tools to governments around the world, announced Wednesday that it can unlock and extract the full file system from locked iPhones including the 6 and 6+ with their Advanced Investigative Service (CAIS) product in which their customers send phones they urgently need unlocked.
Every version before the 6+ can also be unlocked by Cellebrite whose forensic researchers say they have successfully bypassed Apple’s security and encryption.
Cellebrite’s director of forensic research announced the service in a tweet posted Wednesday:
CAIS is the in-house product on sale from Cellebrite. They also offer products like the new version of the Universal Forensic Extraction Device (UFED) Physical Analyzer 6.0 for use in the field by their customers. The company has been increasingly advertising their newest product’s ability to easily extract and investigate data from encrypted secure messengers including Signal, Telegram, Threema and Surespot.
The company charges $1,500 to unlock an individual phone, while a yearly subscription to the service runs for $250,000, according to a report from the Intercept last year.
The ability to unlock the iPhone 6 comes a year after a titanic legal and political battle between Apple and the FBI in which the government pushed the tech giant to write code allowing police to unlock an iPhone 5s used by a shooter in the San Bernardino attack. The confrontation ended when the FBI used unidentified hackers who found another way in. Although unlocking phones was already big business, the headline-making incident accelerated the industry, as well as Cellebrite’s prominence after they were rumored as the company that broke into the iPhone.
Cellebrite, nor the FBI, has never officially admitted their involvement in case related to the iPhone 5s.
Companies like the Israel-based Cellebrite make a mint selling tools to local and federal law enforcement agencies in the United States as well as countries like Turkey, the United Arab Emirates and Russia. Cellebrite began marketing to government authorities a decade ago, a business that’s booming since strong encryption has increased in adoption in recent years.
To top off the new offerings, Cellebrite’s also now targets Uber apps on Android and iOS, a potentially massive source of personal data that includes the user’s account and locations. That’s in addition to the ability to extract and analyze vast mountains of data from apps ranging from Chrome to Facebook to dating apps, all of which can contain extremely private information.
Cellebrite’s ability to break into the iPhone 6 and 6+ comes in their latest line of product releases. The newest Cellebrite product, UFED 6.0, boasts dozens of new and improved features including the ability to extract data from 51 Samsung Android devices including the Galaxy S7 and Galaxy S7 Edge, the latest flagship models for Android’s most popular brand, as well as the new high-end Google Pixel Android devices.
“In the majority of devices, Cellebrite’s proprietary boot loader can bypass all security mechanisms, even if the device is locked, without jailbreaking, rooting or flashing the device,” according to the company. Newer devices, particularly iOS devices, present evolving challenges.
Cellebrite’s new product puts the crosshairs on several other apps used for secure communications including the latest versions of FireChat, Facebook Messenger (which offers Secret Messages using the Signal encryption protocol) and WhatsApp (another app that uses the Signal protocol). Cellebrite’s access to these apps varies from platform to platform, but they offer support for roughly the same amount of iOS and Android apps.
Here’s how a slightly older version (5.5) of Cellebrite’s analyzer presents data extracted from a phone’s messengers:
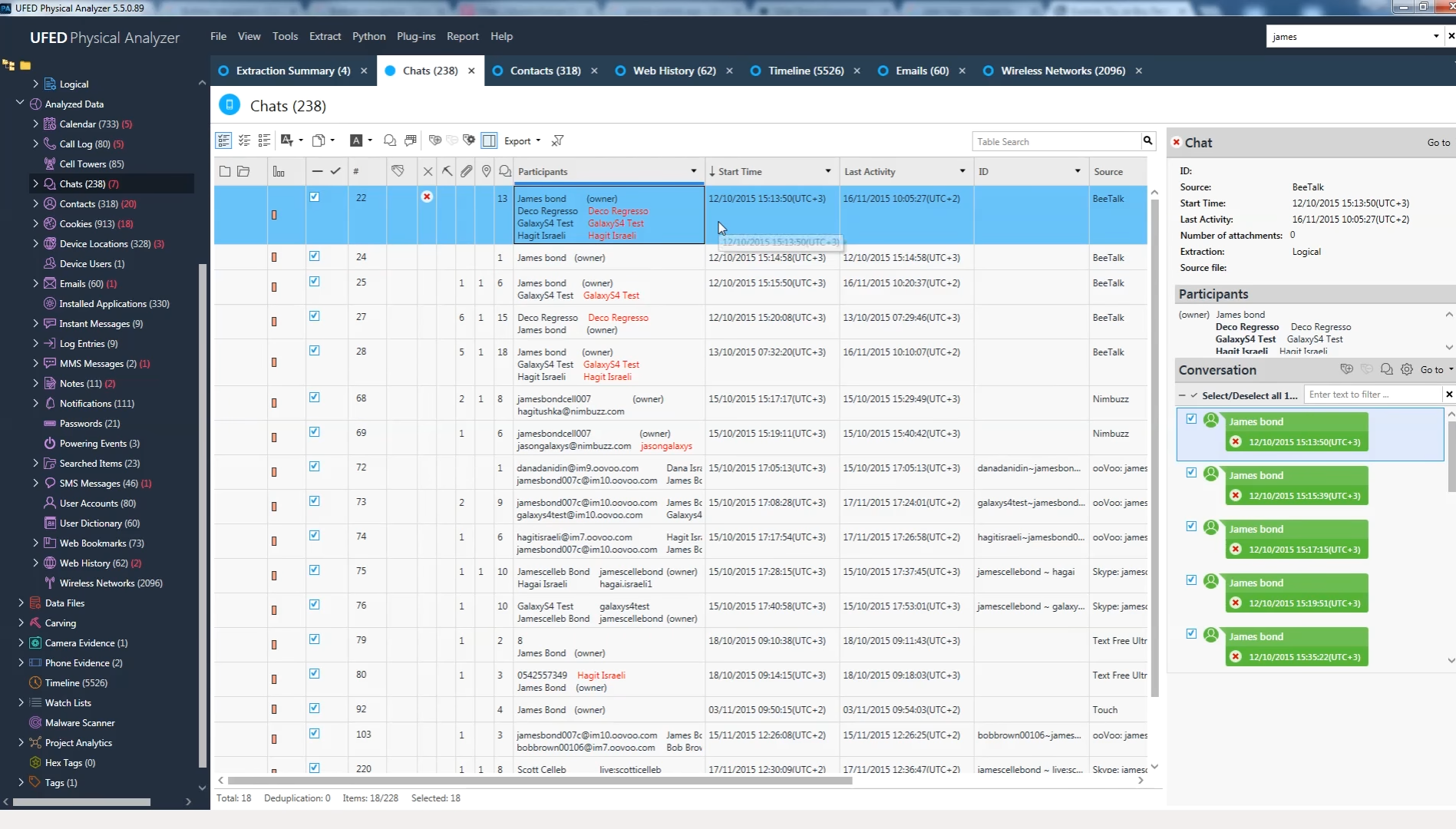
Every new iteration of the UFED Physical Analyzer promises “increased extraction functionality” to make an investigation speedier by putting evidence in the hands of police quicker, overcoming obstacles like a smartphone’s built-in security. Here is a video touting the product:
https://player.vimeo.com/video/198848461
Here is the latest UFED Physical Analyzer 6.0 PDF advertising all the new features the latest version is selling:
https://www.documentcloud.org/documents/3473528-CellebriteAdvertisement.html
Apps like Messenger and ChatLock, which allow users to protect their messengers with separate four digit PIN passwords, are targeted as well.
“These capabilities dramatically increase law enforcement’s ability to access critical digital evidence and solve cases faster, by providing forensically sound access and extraction capabilities not found anywhere else in the industry,” according to the company. “Furthermore, we now makes the world’s first ‘decrypted physical extraction’ capability a reality for key iPhone and Samsung Android devices.”
One of Cellebrite’s product’s key features is to offer direct app support so that users can thoroughly extract and visually map data from any app on a user’s phone including messages, logs and anything else that takes place there. Even deleted data can be made available. You can see how it works here.
Examinations of court documents over the last year show that Cellebrite can break some unprotected Android phones in around 60 seconds. iPhones, on the other hand, can take in between one to two hours, according to law enforcement testimony, although the time needed varies depending on numerous factors. After that, masses of data including text messages, photos and app information are extracted and prepared in a court-ready report for police.
Earlier this month, a hacker dumped 900GB of data stolen from Cellebrite to put the spotlight back on the debate about backdoors into encrypted phones and other devices.
We reached out to Apple and they declined to comment.




