‘BadRabbit’ ransomware spreading across Ukraine, Russia
Multiple Russian and Ukrainian organizations were hit with a ransomware attack Tuesday, causing disruptions across a number of different transportation hubs, including a major airport and transit system in Kiev, Ukraine, as well as several Russian media organizations.
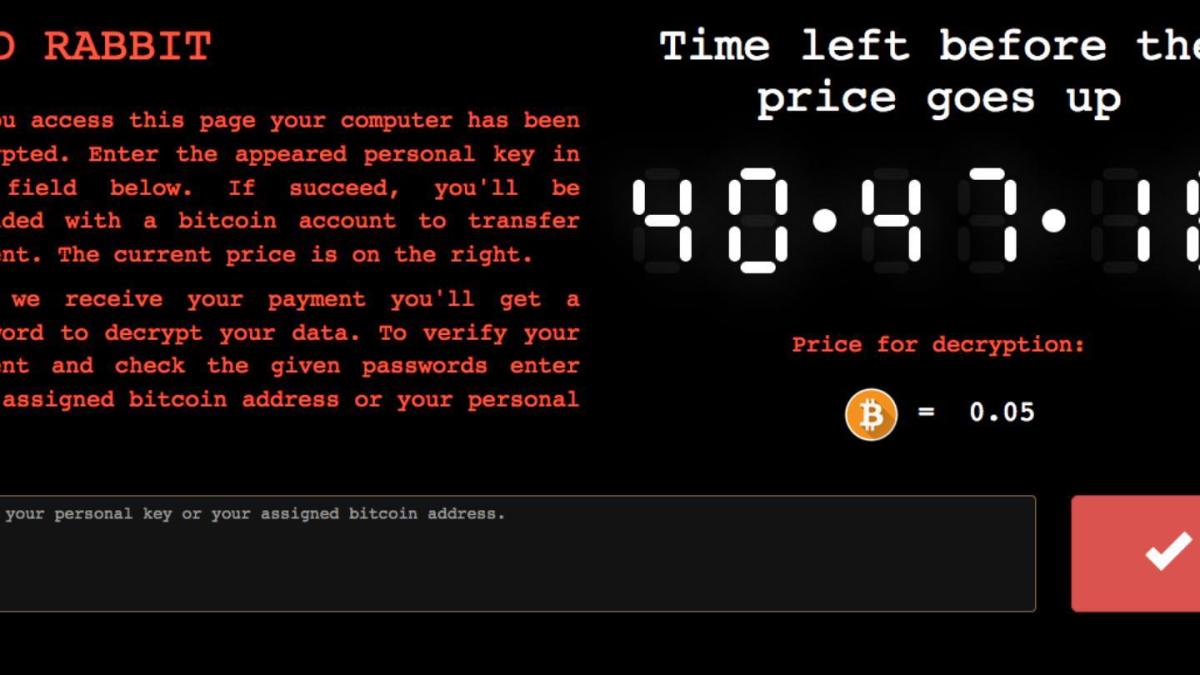
The malware, dubbed “BadRabbit” by security researchers, will load a message in red text over a black background on infected computers, requesting payment from victims in order to unlock their systems. The price to unlock an infected system increases over time, the message reads, and the malware requires victims to log into a Tor hidden service website to send bitcoin.
This display carries certain similarities with another ransomware outbreak known as NotPetya, which spread across Ukraine in June and into a variety of multinational corporations with connections to the country’s economy. Other overlaps also exist between NotPetya and BadRabbit, including the reuse of Diskcoder.D, a trojan that encrypts files on local drives, researchers say.
Jay Rosenberg, a senior security researcher with Israeli cybersecurity firm IntezerLabs, found that BadRabbit uses copied code from NotPetya.
According to Czech cybersecurity firm ESET, the attackers behind BadRabbit incorporated the post-exploitation software tool Mimikatz into the ransomware in order to extract credentials and help their attacks spread. At the moment, researchers believe the malware was distributed via a fake Adobe Flash player in some cases.
Based on a blog post published by ESET shortly after news broke, BadRabbit has infected computers belonging to “Kiev Metro, Odessa naval port, Odessa airport, Ukrainian ministries of infrastructure and finance, and also a number of organizations in Russia are affected.”
Although most of the damage appears to be concentrated in Ukraine and Russia, it’s not yet clear how widespread the issue has become. ESET was able to find indicators of Diskcoder.D infections in Turkey as well.
At least three different Russian media outlets, including news publishers Interfax and Fontanka, were affected by BadRabbit Tuesday, according to IB Group, a Russian cybersecurity firm.
In a statement sent to CyberScoop, Moscow-based cybersecurity firm Kaspersky Lab said that BadRabbit’s biggest footprint was in Russia.
“According to our data, most of the victims targeted by these attacks are located in Russia. We have also seen similar but fewer attacks in Ukraine, Turkey and Germany,” Vyacheslav Zakorzhevsky, head of Kaspersky Lab’s anti-malware research team.
“This ransomware infects devices through a number of hacked Russian media websites. Based on our investigation, this has been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack,” Zakorzhevsky said. “However we cannot confirm it is related to ExPetr. We are continuing our investigation.”
ExPetr is the name used by Kaspersky for NotPetya, which ESET eventually linked to a hacker group associated with Russia named Telebots. In the NotPetya case, researchers also found that the ransomware was designed primarily to destroy data rather than for financial gain.
Ukraine’s primary cybersecurity authority, the Security Service of Ukraine, did not respond to a request for comment.
A security researcher with ESET, Lukas Stefanko, indicated on Twitter that BadRabbit may be able to spread directly to systems that are connected to infected machines because the ransomware exploits a vulnerability in Microsoft’s SMB process, which continues to exist in older Microsoft operating systems.
https://twitter.com/GossiTheDog/status/922874317964304384
Answering how BadRabbit arrived onto all of the systems infected with the virus remains a mystery. There’s multiple theories and likely more than one cause, experts say.
“Right now we can confirm the following spreading mechanism: remote execution on an infected network. The malware obtains the credentials needed for that: 1) by using the infamous Mimikatz password extraction tool (which the malware drops and executes) and 2) using a username-password combination list hardcoded in the binary,” Robert Lipovsky, a senior malware researcher with ESET, told CyberScoop. “The analyzed samples use the SMB protocol with those hardcoded credentials, but no EternalBlue or any other SMB exploit was found.”
“It is possible that the main targets (critical infrastructure like subway, airport, government organizations, etc.) were compromised some time ago, before this orchestrated ransomware attack occurred today,” he said.
EternalBlue is a high-quality software exploit that has been linked to the NSA and which was published online for use earlier this year by a mysterious group known as The Shadow Brokers.
“While investigating other possible infection vectors, we also discovered a dropper of Win32/Diskcoder.D in the form of a fake Flash Player installer, which we have observed on major news websites in Russia and Ukraine,” said Lipovsly. “While this may very well be an infection vector, it is doubtful that this was ‘the’ main infection vector and it could quite possibly be a smoke screen.”
While a booby-trapped pop-up advertisement — designed to look like an Adobe Flash installer — planted on compromised websites represents a known infection vector for BadRabbit, there could be other channels for how it entered computers. The fake Adobe message is likely just one part of a larger operation.
Kaspersky Lab confirmed some of Lipovsky’s findings via a company blog post released late afternoon Tuesday: “the ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites.”
This is a developing story and will be updated as information becomes available.




