Newly uncovered Iranian hacking group targeted energy, aerospace firms to steal secrets
A Iranian hacking group has been targeting aerospace and energy companies in Saudi Arabia, South Korea and the U.S. since at least 2013 as part of an expansive cyber espionage operation to both gather intelligence and steal trade secrets, according to new research published Wednesday by U.S. cybersecurity firm FireEye.
This advanced persistent threat group (APT) is labeled APT33 by FireEye. Wednesday’s report offers a distinct and rare view of the group’s recent activity. The Iranian hacking team is likely related to a campaign that was separately identified in March and codenamed “StoneDrill” by Kaspersky Lab. Based on information that appears to have been accidentally left behind in past attacks, analysts believe APT33 is linked to the Iranian government.
Most of the group’s operations to date have largely focused on sending targeted phishing emails with malware-laden HTML links to infect computers with a custom backdoor implant known as “TURNEDUP.” But there’s also some evidence to suggest they’re capable of launching data wiping attacks against valuable, infrastructure companies.
A dropper that APT33 uses, known as “DROPSHOT,” is connected to a data destroying malware variant that has been launched in the past by other Iranian hacking groups. The sharing of tools may represent a connection between APT33 and other, known entities.
“Although we have only directly observed APT33 use DROPSHOT to deliver the TURNEDUP backdoor, we have identified multiple DROPSHOT samples in the wild that drop SHAPESHIFT,” a research report by FireEye reads. “The SHAPESHIFT malware is capable of wiping disks, erasing volumes and deleting files, depending on its configuration.”
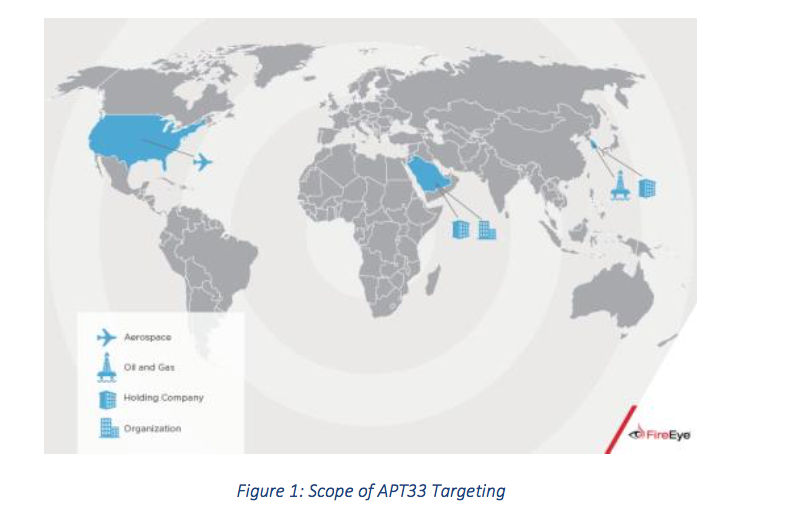
APT33 targeting profile – graphic via FireEye
APT33 registered multiple domains to masquerade as aviation companies and Western defense contractors. These websites were designed to appear like legitimate Saudi businesses ventures, but they instead led to fake information. The domains could have been used in phishing emails to bolster their appearance to victims.
“From our side, this looks like classic espionage with maybe the option for something more destructive in the future,” said John Hultquist, director of intelligence analysis with FireEye. “It shows [Iran] is making a concerted effort to build cyber capabilities for use by different teams.”
This is not the first time Iran has been blamed for sponsoring cyber espionage operations against foreign nations. Prominent cybersecurity firms, including Symantec, Kaspersky Lab, FireEye, RSA and Palo Alto Networks, have each identified data breaches in the past that carried indicators of Iranian hacking groups; which were subsequently codenamed NewsCaster, RocketKitten and GreenBug.
FireEye’s findings serve to highlight the apparent and ongoing investment made by the Iranian government to build an adept force of professional hackers capable of remotely gathering intelligence, launching disruptive attacks and stealing intellectual property.
In a recent public appearance in D.C., Dmitri Alperovitch, co-founder of U.S. cybersecurity firm CrowdStrike, told an audience of Washington insiders that Iran was increasingly conducting economic espionage to boost its economy. CrowdStrike is perhaps best known for its work with the Democratic National Committee.
Hultquist said FireEye had personally responded to six different incidents where APT33 was responsible for attacking an organization. He noted that FireEye is likely only aware of a small percentage of breaches conducted by APT33, but declined to speculate on the number of businesses that could be impacted.
Researchers were able to successfully piece together a failed APT33 email phishing attempt to identify details about the author’s original username, “xman_1365_x.” According to FireEye, this “xman” pseudonym has been active on Iranian internet forums, including a software engineering message board used by hacktivists, and was at some point connected to the Nasr Institute.
The Nasr Institute is “equivalent to Iran’s ‘cyber army’ and controlled by the Iranian government,” FireEye notes in its research report about APT33. “Additional evidence ties the ‘Nasr Institute’ to the 2011-2013 attacks on the financial industry, a series of denial of service attacks dubbed Operation Ababil.”




