Apple ramps up war on spyware, a growing digital scourge

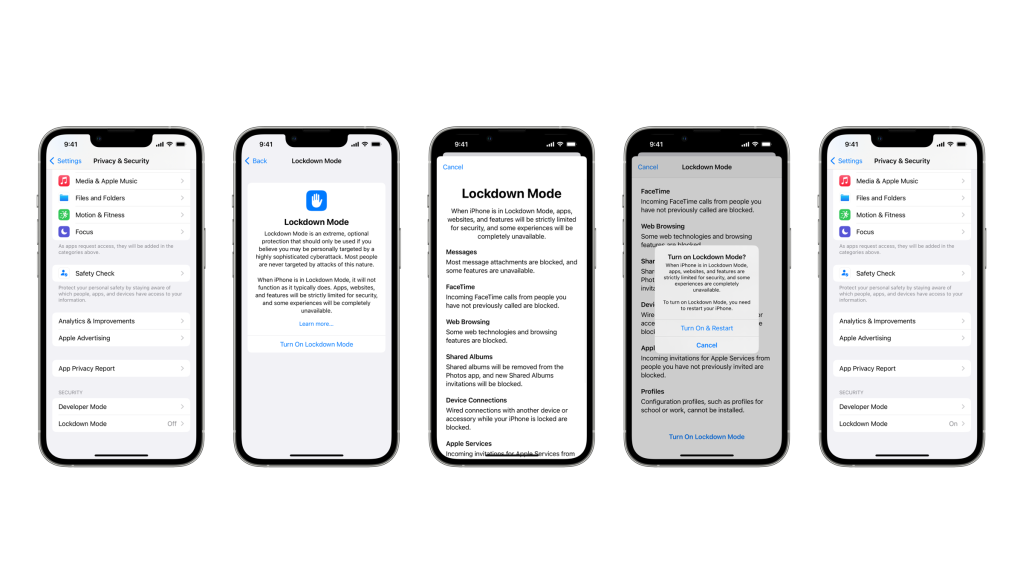
Apple will introduce a feature this fall allowing users to lock services that could otherwise be exploited by malicious hackers looking to infect their phones with spyware. While the company expects that ultimately only a fraction of its users may need the optional layer of enhanced security, the tool highlights Apple’s ongoing fight against the growing global spyware industry.
Apple’s “Lockdown Mode” is intended to make it harder for attackers to take over a victim’s phone through steps such as blocking most forms of message attachments and preventing unknown connections with a computer or accessory.
The announcement comes less than a year after researchers at the University of Toronto’s Citizens Lab discovered an iOS exploit dubbed FORCEDENTRY, which they attributed to the NSO Group, an Israeli technology company known for its surveillance software. The exploit allowed hackers to remotely install NSO Group’s Pegasus spyware on iPhones. Apple then sued NSO Group for allegedly developing the exploit. NSO Group has denied any wrongdoing and the lawsuit is ongoing.
Spyware has become a growing global problem, affecting politicians, activists, executives and victims of domestic abuse. An Apple representative said that the company has alerted potential victims of highly targeted mercenary spyware in nearly 150 countries. The spokesperson declined to share how many individual victims the company has notified, citing ongoing litigation with NSO Group. Apple began notifying suspected NSO Group victims in November.
Some users will be able to soon access a beta version of Lockdown Mode, a move that Apple is hoping will attract security researchers’ input, too. The company is incentivizing security researchers to report any bugs by doubling its normal bounty to up to $2 million dollars.
NSO Group has been under pressure from human rights organizations for reportedly providing the software used to hack the phones of dozens of activists, journalists, dissidents and politicians worldwide on the behalf of nation-states and other powerful customers. Hacking victims have included, Polish political candidates, journalists across the Middle East and phones reportedly associated with the U.S. State Department.
The company has attracted government scrutiny, too. The U.S. Commerce Department in November added NSO Group and one other Israeli spyware firm to a list of designated national security threats. And Meta-owned WhatsApp sued the company in 2019, alleging the company’s technology was used to spy on WhatsApp users.
In addition to its anti-spyware feature, Apple announced it is awarding a $10 million grant, in addition to any damages awarded from the lawsuit filed against NSO Group, to a new fund established by the Ford Foundation, the Dignity and Justice Fund. The fund’s advisory committee includes representatives from Amnesty Tech, Access Now and Citizen Lab, all groups that have investigated NSO Group spyware.
The fund could be used to expand efforts by a number of global organizations researching spyware, especially in the global south, Ron Deibert, director at Citizen Lab, told reporters in a call Tuesday.
“The more we have groups doing this type of digital accountability watchdog work, the less harm will be caused in the long run,” said Deibert. “We need this kind of protective net and the only way that can be done in order to preserve the independence of the mission is through philanthropic foundations like Ford Foundation.”




