Scammers make millions in two months with dated Android exploits

A newly discovered strain of Android malware earned hackers $1.5 million, with researchers pointing to a Chinese ad firm as possibly being responsible for the malware’s spread.
The malware, called CopyCat, infected 14 million Android devices, rooted 8 million phones and had 3.8 million devices serve ads, according to the Israeli cybersecurity firm Check Point Technologies. Victims were mainly in South and Southeast Asia, but over 280,000 Android users in the United States were also infected.
India was the hardest hit nation with over 3.8 million victims from the CopyCat campaign.
Researchers from Check Point released a report on the threat on Thursday calling out CopyCat’s “unprecedented success rate.”
CopyCat uses an arsenal of exploits that are, at the most recent, two years old. The oldest exploit, CVE-2013-6282 (VROOT), dates back to 2013. The success of the campaign is a testament to the fact that millions of users are operating old, unpatched and unprotected devices that are indefinitely in danger from attacks that have long since been made public.
This is a problem that hits Android particularly hard because, unlike Apple’s iOS devices, Android’s ecosystem is fragmented in a way that often negatively impacts security.
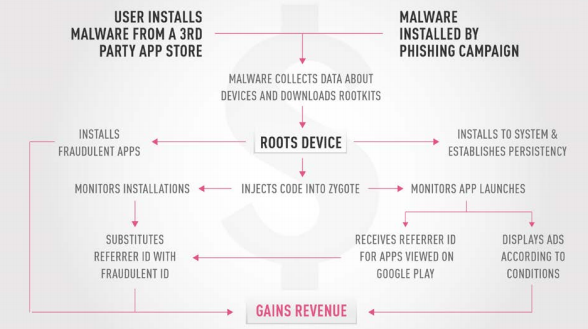
“CopyCat is a fully developed malware with vast capabilities, including rooting devices, establishing persistency, and injecting code into Zygote — a daemon responsible for launching apps in the Android operating system — that allows the malware to control any activity on the device,” the researchers wrote.
(Check Point)
After infection, the malware roots the victim’s device to gain full control and remove defenses. CopyCat uses Zygote to fraudulently install apps and display ads so it can collect profits estimated by the researchers to reach about $1.5 million during the peak of activity during April and May 2016.
Over $735,000 of the profit came from the 4.9 million app installations. The tactic takes advantage of advertisers paying premiums for ad displays that lead to app installation. CopyCat specifically targets the mobile ad firm Tune.
The campaign has ended due to action by Google, the company said, but infected devices could still be impacted by the malware.
Check Point researchers pointed to MobiSummer, a Chinese ad network, as having “several connections” to the attack’s shared infrastructure, malware code signed by MobiSummer and remote services used by the malware that were created by MobiSummer. Additionally, the malware didn’t target Chinese devices despite over half of the victims residing in Asia.
The company did not respond to a request for comment.
The malware also avoids interfering with major apps like Facebook and WhatsApp for unknown reasons.
Users worried about campaigns should make sure to use devices that have the latest security patches. For many low income Android users around the world, that’s often not an option because cheaper and older Android devices stop receiving security updates long before they go out of use.






