Hackers target ‘hundreds’ of Middle East activists with fake login pages, 2FA bypass schemes

Hackers have been going after email accounts of hundreds of Middle East-based human rights activists, journalists and others using methods that bypass security features of services like Google, Yahoo, ProtonMail and Tutanota, according to a report published Wednesday by Amnesty International.
The human rights watchdog says its likely that a single group of hackers has been using clever pages that mimic secure login pages, as well as tricks that bypass two-factor authentication (2FA) to target accounts at least throughout 2017 and 2018. The targets are mostly in the United Arab Emirates, Egypt, Yemen and Palestine, the group said.
“What makes these campaigns especially troubling is the lengths to which they go to subvert the digital security strategies of their targets,” the group says in the report.
Amnesty International analyzes the activity as two separate campaigns. One uses fake pages that look like they belong to ProtonMail and Tutanota in order to get users to hand over their credentials. The other uses fake security alerts to trick Google and Yahoo users into sending valid credentials and SMS-based 2FA codes.
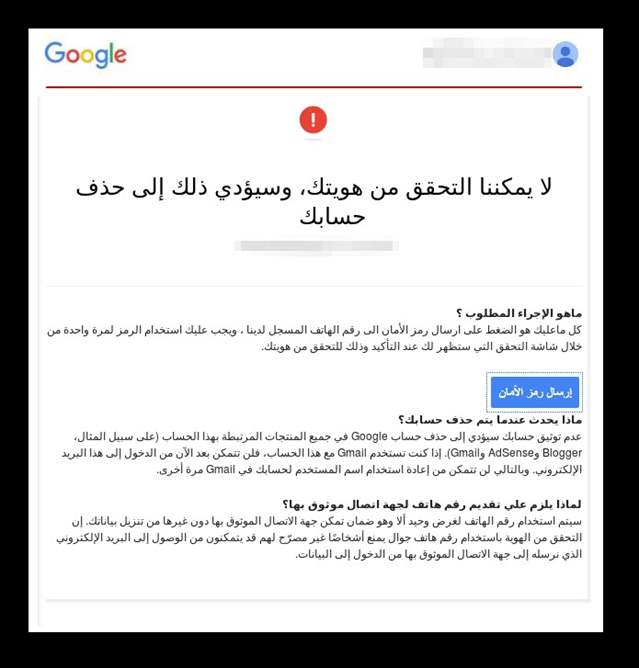
In the scheme targeting Google and Yahoo accounts, hackers compel a target to hand over their credentials via a fake webpage. On the back end, that sets off a string of automated processes. 2FA codes normally expire within minutes if not seconds, and the report says the hackers have targeted around a thousand victims. To achieve this scale, the campaign’s apparatus has to automatically follow all the legitimate steps involved with 2FA, while serving a mirrored process to their victims. The victim is tricked into plugging in the real 2FA code into another fake page owned by the hackers.
The hackers then gain persistence using an app password — a legitimate tool that lets people use email through third-party apps like Outlook or Thunderbird — which instructing the victim to finally change their password. The last step is just for show, the report said.
“The purpose of taking this additional step is most likely just to fulfill the promise of the social engineering bait and therefore to not raise any suspicion on the part of the victim.”
Beyond that, the attackers also used a commercial service called ShuttleCloud to clone Yahoo victims’ contacts and messages in a separate Gmail account that the attackers control.
Many savvy users would notice if a security alert or login page is actually a scam. But Amnesty International says the attackers are using their targets’ wariness to their advantage.
“This approach exploits their fear and instills a sense of urgency in order to solicit a login with the pretense of immediately needing to change their password in order to secure their account. With [human rights defenders] having to be constantly on the alert for their personal and digital security, this social engineering scheme can be remarkably convincing,” the report says.
A fake Google alert written in Arabic says “We are not able to verify your identity, and this could result in the termination of your account.” (Amnesty International)
In the campaign targeting the ProtonMail and Tutanota accounts the hackers obtained domains that look deceptively like the legitimate ones, like “tutanota[dot]org” instead of “.com” and “protonemail[dot]ch” with an added “e.” Those websites looked identical to the real ones.
“Many users rightfully expect that online services control the primary .com, .org and .net domain variants of their brand. If an attacker manages to acquire one of these variants they have a rare opportunity to make the fake website appear significantly more realistic,” the report says. “These elements, together with an almost indistinguishable clone of the original website, made this a very credible phishing site that would be difficult to identify even for the more tech-savvy targets.”
The methods the attackers are using are not new, but the report shows that the hackers are automating these processes in a way that highlights the depths to which groups will go to spy on activists and other targets.
The report shows that while SMS-based 2FA is useful layer of security that can thwart phishing attempts, determined attackers can get past it with enough trickery. The report cautions that hackers can even get past push notification-based 2FA with enough automation, and that physical keys Yubikeys are likely the most secure authentication method.
“Don’t be mistaken, two-factor authentication is important and you should make sure you enable it everywhere you can. However, without a proper understanding of how real attackers work around these countermeasures, it is possible that people are misled into believing that, once it is enabled, they are safe to log into just about anything and feel protected,” the report says.



