Scammers are abusing mobile ad networks in an attempt to phish Android app users

A network that delivers ads to hundreds of Android apps also is directing users to malicious websites that could help scammers steal their information or overrun their device with spam.
At least 400 apps in Google’s Play Store come embedded with proprietary software that is designed to help app developers monetize their program by serving ads. Scammers are exploiting that process, though, by inserting malicious ads into the software development kits (SDKs) that are meant to help developers earn a living.
Domains and URLs sent in ads from the distribution framework known as StartApp flood users with links to malicious sites or push notifications for spam, according to new findings from mobile security firm Wandera provided exclusively to CyberScoop. StartApp, created and run by a New York-based marketing firm, does not appear to be behind any malicious content, though it is compensated by other firms that supply it with the malicious ads. StartApp did not respond to questions about the content it pushes through its service.
“Our researchers wanted to explore a service that wasn’t associated with a single well known advertiser, such as Google or Facebook, so they took a closer look at the framework from StartApp, which would presumably provide app developers with ads from a wider variety of advertising networks,” the Wandera report noted.
The company is one of numerous firms offering SDKs that connect app developers with advertising companies. It claims its technology is integrated with 19% of all ad-supported Android apps, giving its advertising partners valuable reach into the global smartphone market. StartApp is a legitimate company widely used through Google’s app market, though, like other providers, some of the ads it sources slip through security checks.
Roughly 90% of the ads displayed through the StartApp framework are obtained from a single advertising provider, according to Wandera researchers.
While Wandera did not identify that advertising provider by name, CyberScoop has independently confirmed that the provider is AdSalsa, a digital marketing company headquartered in Spain. AdSalsa is the source of many of the advertisements that try to direct users to dangerous websites.
“The network consists of a large number of globally distributed servers and diverse domain names that allow the ad network to hide behind multiple subsidiaries, physical and internet-based,” Wandera states.
The scheme takes advantage of the network’s structure: Advertisers pay AdSalsa to funnel ads toward apps. AdSalsa passes those ads along to StartApp, which claims to be used by 800,000 software programs. It’s a common process that’s only unusual in this case, researchers say, because an unusually high number of ads direct users toward suspicious websites, apparently without proper vetting by either AdSalsa or StartApp.
“There is no single bad actor here that we can say with certainty is doing an intentionally bad thing on their own,” said Michael Covington, vice president of product at Wandera.
The apparent malfeasance only is the latest evidence that the complex mobile advertising ecosystem has made it possible for attackers to spread malware and leverage infected devices for their own intelligence collection. (AdSalsa did not respond to multiple requests for comment from CyberScoop.)
One app, which promised to inflate a user’s follower count on TikTok, sent ads to 15 individual domains classified as “malicious,” “phishing, “suspicious” or “spam” in VirusTotal’s malware database. The app was called “Get Free Fans for Tik, Followers & Likes for Tok” before it was removed from the Play Store. Security researchers determined that the program attracted more than 50,000 downloads while also overwhelming users with links to unsolicited adult content and games requesting their personal data.
Ads on other apps promised free iPhones to users who provided their personal information and credit card details. At other times, full-screen ads urged users to enter their financial data in exchange for Amazon gift cards worth hundreds of dollars.
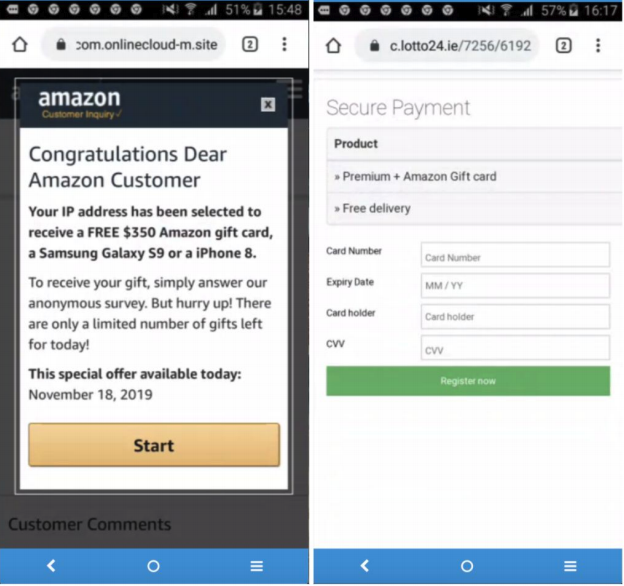
An ad that appears to be from Amazon promises $350 for unwitting victims (Wandera).
Other applications including the StartApp framework remain active on the Play Store, according to Wandera. One program, “APUS Launcher Pro- Theme, Live Wallpapers, Smart,” counts more than 500,000 downloads, and appears to be a product from APUS Group, a Chinese technology company. Other apps, such as “Undeleter Recover Files & Data,” boast more than 10 million downloads, though many of the reviews complain about the number and size of the ads that come with it.
At least some of the apps that were removed have re-appeared, such as the “Get Free Fans for Tik” app, which appears to have more than 100,000 downloads since another version of the program surfaced in March.
Wandera researchers detected 699 apps on the Play Store using StartApp’s SDK, though Google has already removed 47% of those programs, the company said.
The 47% removal rate is a “significantly higher percentage than what we see in other application hosting environments,” Wandera told CyberScoop.
Malvertising represents an ongoing headache for security gatekeepers trying to safeguard Google’s app marketplace.
Security researchers this week determined that hackers with connections to the Vietnamese government had, for four years, used Play Store apps to target 300 devices in roughly a dozen countries as part of an espionage campaign. Mobile security pros, meanwhile, regularly announce takedowns of batches of applications that developers deploy for nefarious purposes.
In this case, no single developer appears to be to blame.
The complexity of the online advertising world has made it so that nine different entities may be involved in the chain of serving an individual user with a single ad, industry executives previously told CyberScoop. Each point in the process provides scammers with an opportunity to subvert the protocol for their own gain.
“Exploring mobile advertising is like unraveling an onion with the ads themselves at the core,” researchers said in their report. “Where’s the smoking gun? We don’t know.”




