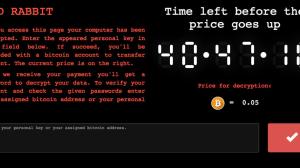
Ukrainian officials: Hacked auto-updates spread ransomware infection across country
As the whole world deals with another massive ransomware outbreak, it appears the variant may have spread in different ways among the various impacted countries.
In Ukraine, the hardest hit nation in Tuesday’s outbreak, the ransomware spread across government institutions, banks and even radiation monitoring at the Chernobyl nuclear facility. The initial attack vector has been attributed to a software update from accounting company MeDoc, which sent an infected file out to customers, according to Ukrainian officials as well as security researchers at Kaspersky and Cisco.
MeDoc acknowledged Tuesday afternoon the company was targeted by “a massive hacker attack,” but denied that the software updates were the infection vector that allowed the malware to spread across the country.
The company did not respond to a request for comment.
Aleks Gostev, Kaspersky Lab’s Chief Security Expert, wrote sardonically on Twitter that MeDoc’s response was merely the first stage of grief: “Denial.”
“We have logs,” Gostev said, pointing to proof of the assertion obtained by Kaspersky. “Unfortunately, I cannot release it in public.”
https://twitter.com/craiu/status/879727503157473281
“Another interesting coincidence,” Nick Bilogorskiy, senior director of threat operations at Cyphort, told CyberScoop. “In Ukraine tomorrow is a holiday – June 28 – Constitution Day. Hackers are known to seed malware outbreaks right before the holidays, to make the recovery take longer.”
The infection vectors for other countries remains less clear. Rosneft, the giant Russian energy firm that was infected earlier on Wednesday, was likely not using the Ukrainian tax software.
Finding out how the malware spread in each region of the globe is perhaps the biggest question among many for cybersecurity experts as Petya continues to inflict damage.